Hawat (Proving Grounds) Walkthrough
Next up is Hawat. If you have seen my other vulnerable practice pentest machine walkthrough, you know the drill, so let's go!
Scanning
We'll start with the nmap scan
nmap -sC -sV -p- --script vuln [target IP]
We see that this is full of interesting services in unusual ports (that is why we use the -p- option in our nmap scan, we should scan all ports, not just the default subset.
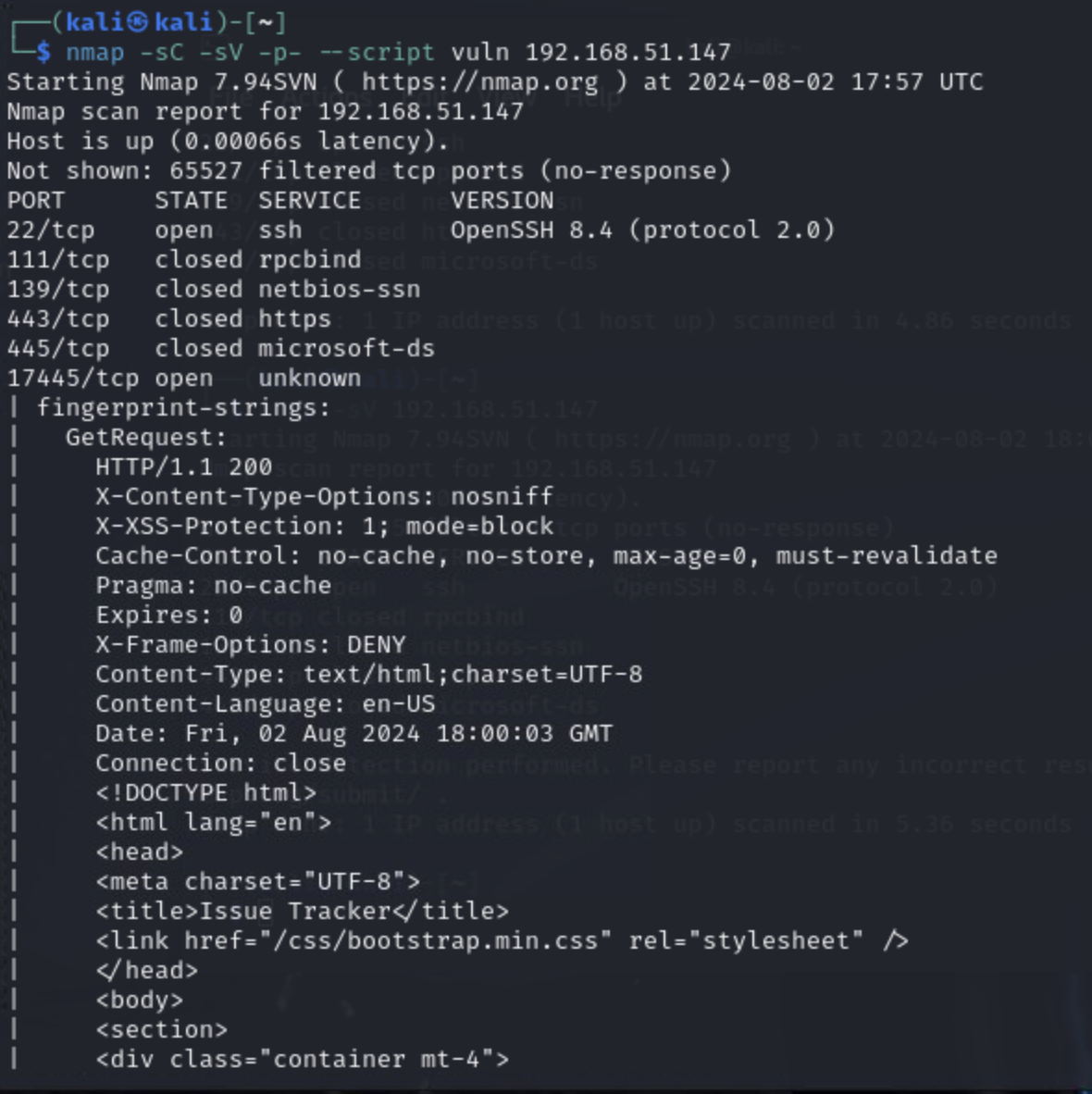
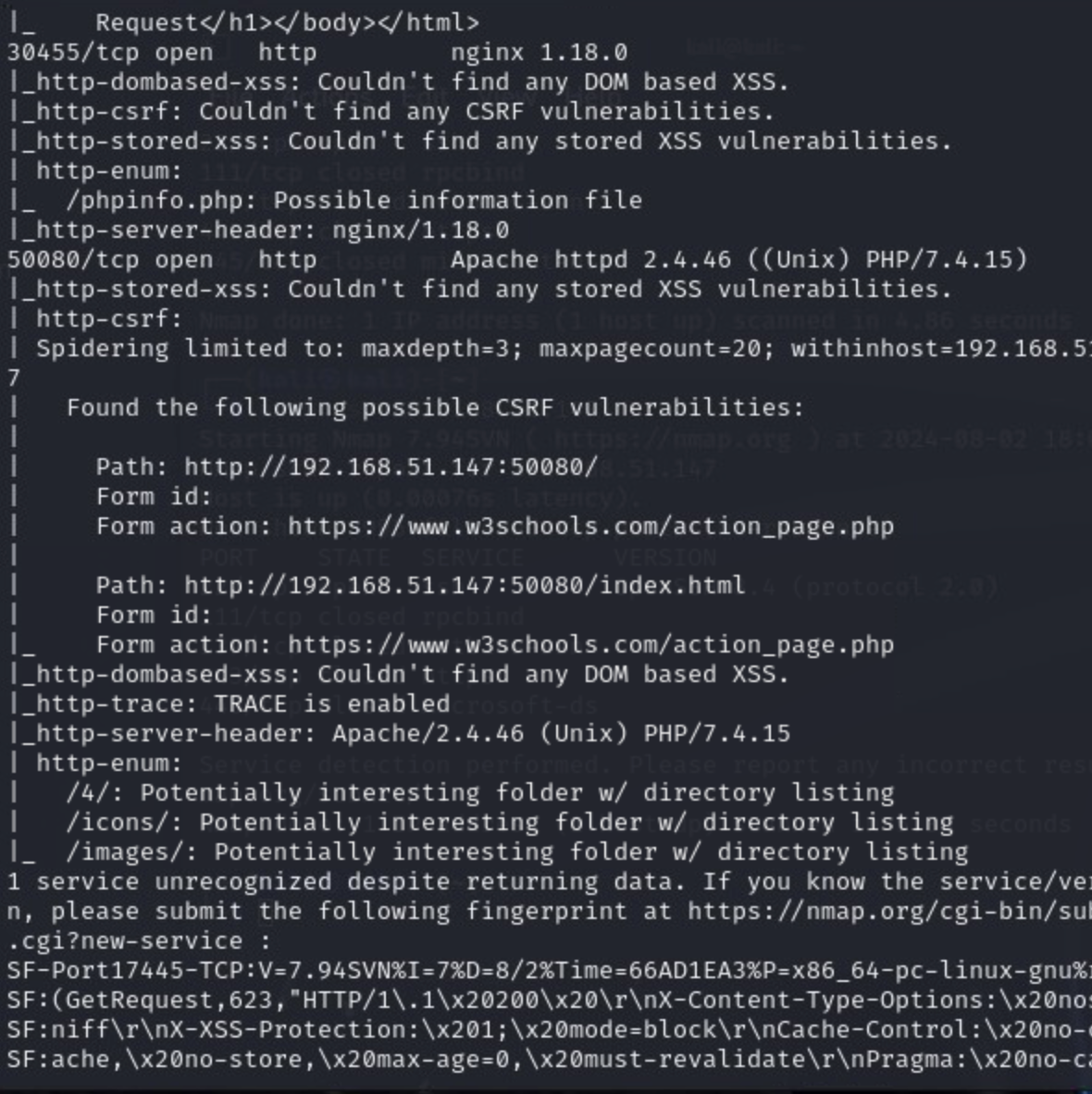
Additional Recon and Enumeration
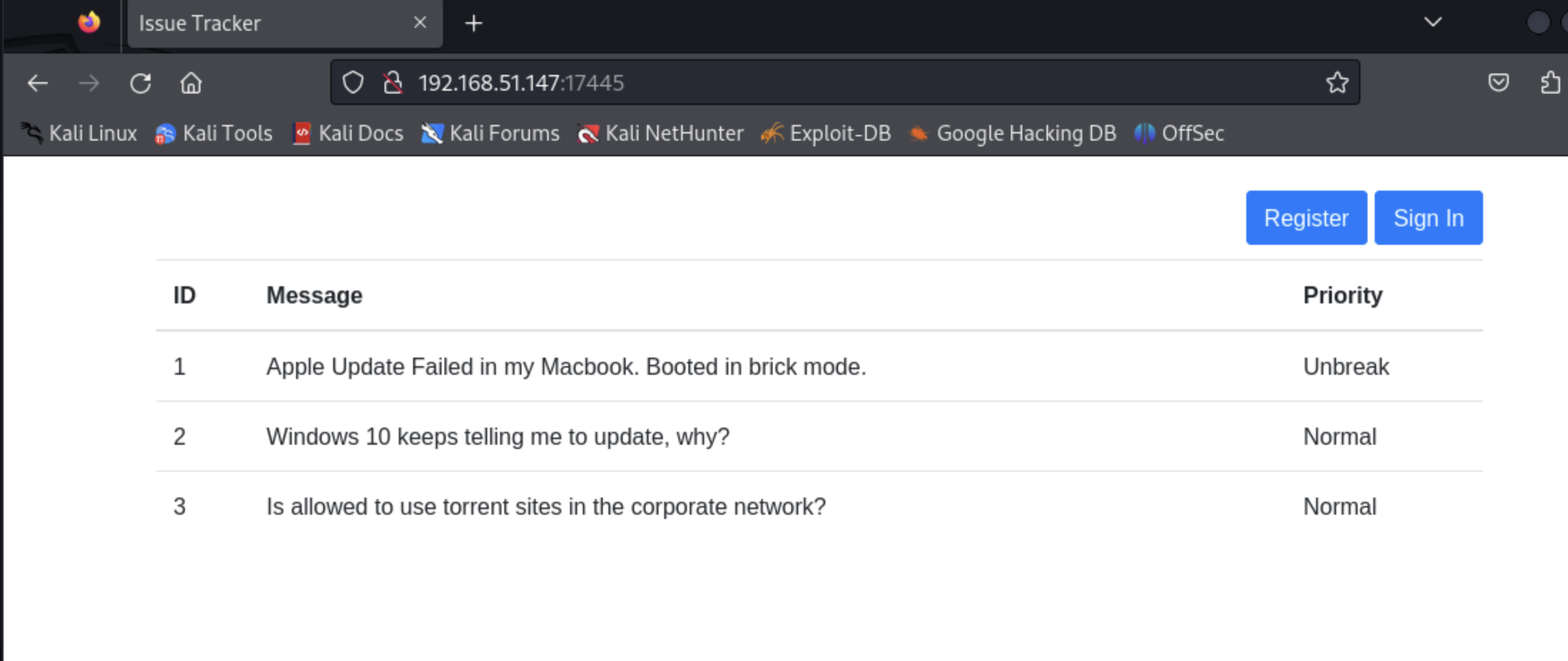
Issue tracker web app in an unusual port, 17445, interesting...
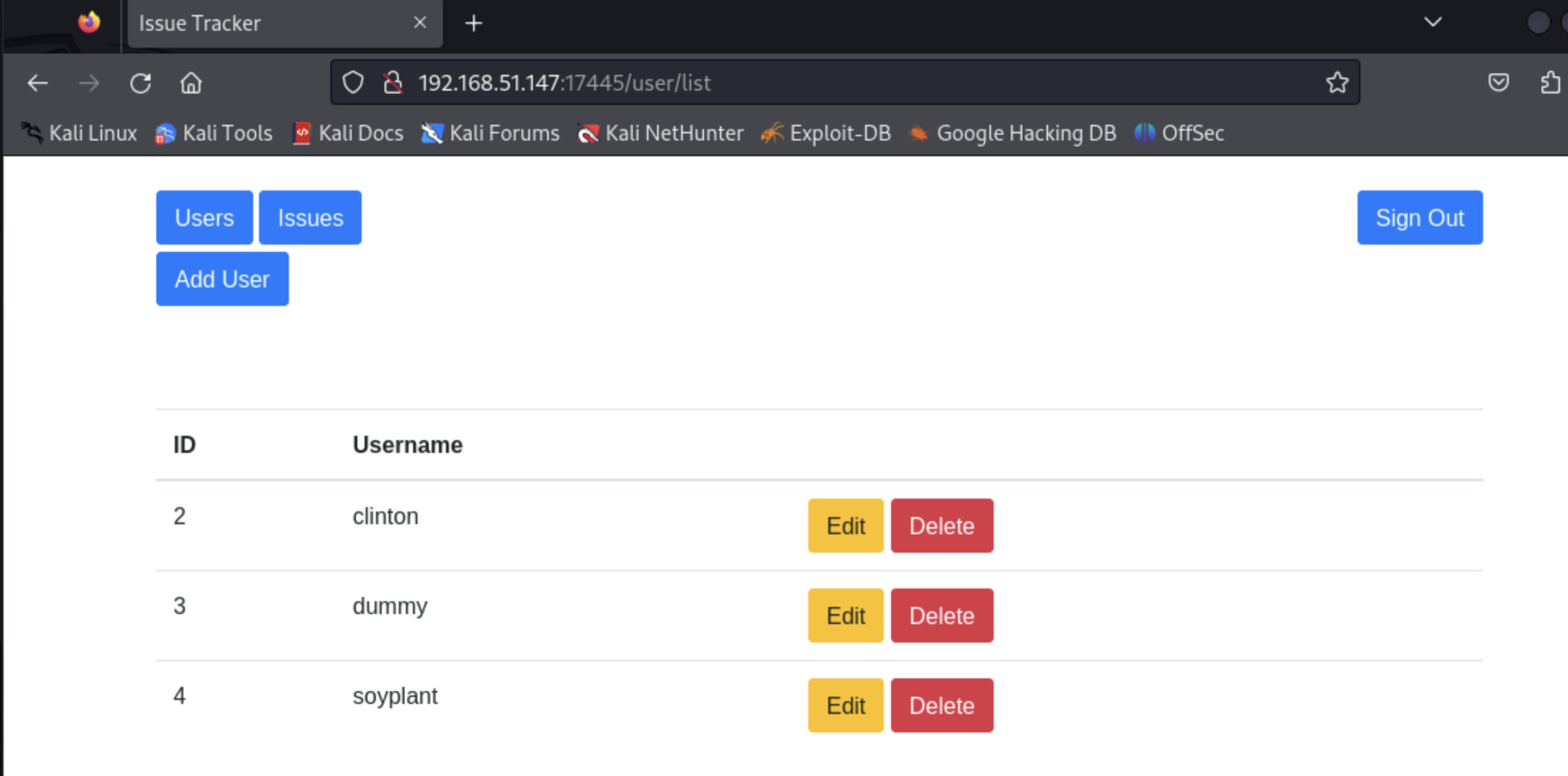
We used the option to create a user on this app (username "soyplant"). Looking at the list of registered user, we see the user we just created as well as a the other existing users (as part of our enumeration)
And another web app on port 30455, also an non traditional port (looks like this is a badly executed attempt to hide apps using non-traditional ports, always a dumb idea!
And another one in port 50080 (yawn?)
And directory traversal over the Internet is allowed, another strike!
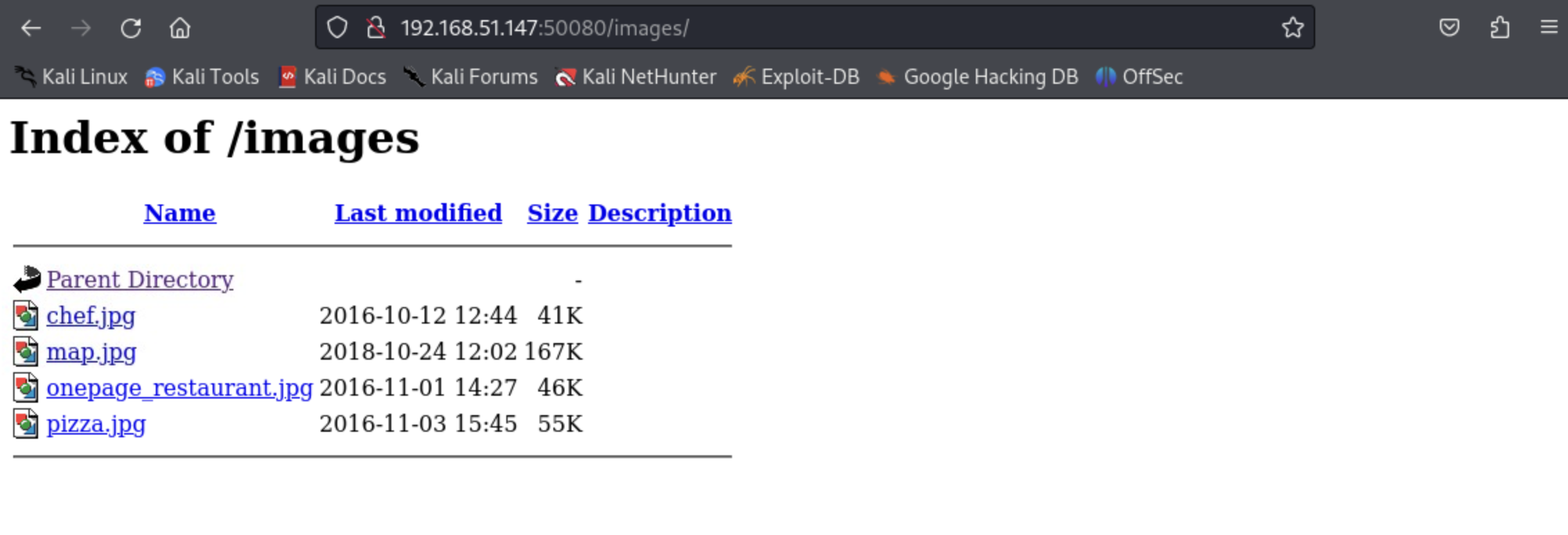
With so many potential attack surfaces, the challenge is which one to pick first. You don't want to go down a rabbit hole and waste a lot of time in what should be a pretty easy machine to exploit!
Let's enumerate some more then, gobuster to the rescue!
Note that if you use the in-browser instance at Proving Grounds, your machine may not have gobuster installed and you will not have privileges to install it yourself. Just like at any time, never depend on a tool! The concept is enumerating a web server and luckily there are other tools you could use if you know how to do web server enumeration in general. In this case, I stumbled upon dirb when looking through the tools installed in the Kali in-browser instance, so let's use that!
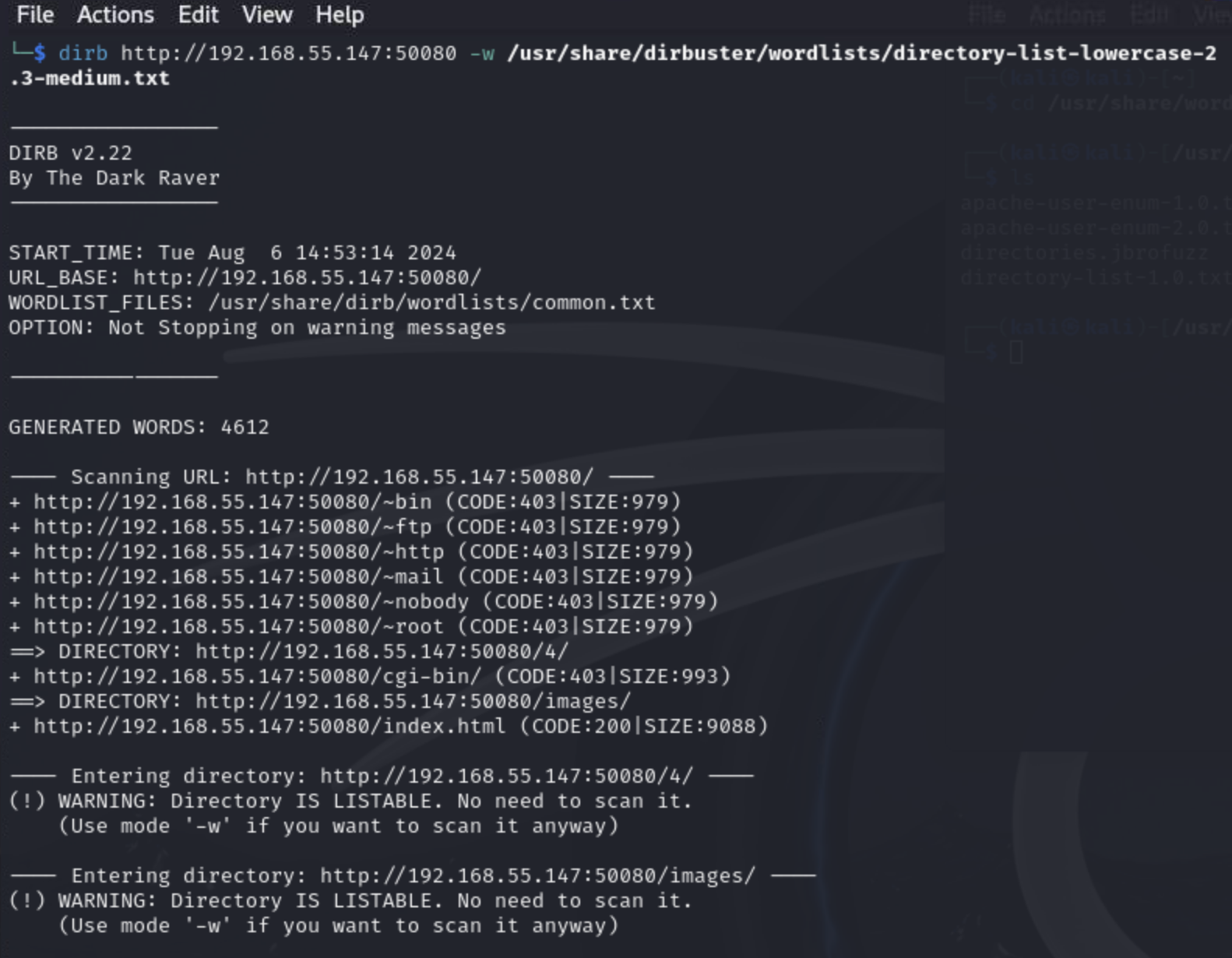
In this case, we will use the command:
dirb http://192.168.55.147:50080 -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
We find the /cloud directory so time to browse it!
There is the Nextcloud login screen:
The combination admin:admin works to log in.
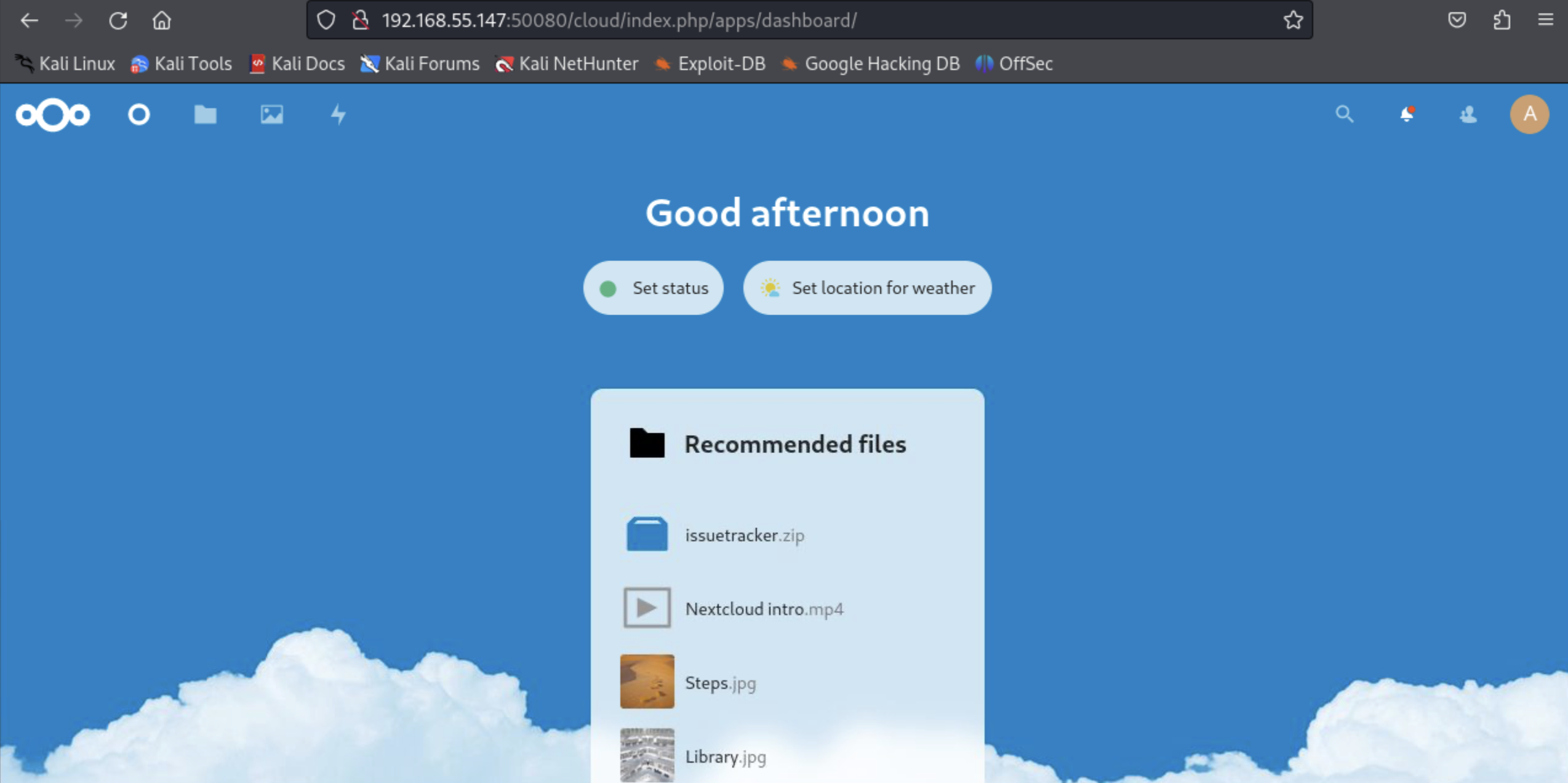
Notice the file issuetracker.zip.
--- TO BE CONTINUED ---